Resources
Another Big Name Falls Victim to Extortion Using Stolen Credentials
By Rodman Ramezanian - Global Cloud Threat Lead, Skyhigh Security
August 15, 2022 3 Minute Read

— Stolen Cisco employee’s credentials and VPN access underscore the risks of authentication misuse
Hot on the heels of numerous high-profile breaches at the hands of cybercrime gangs, Cisco undoubtedly takes no pleasure in confirming a breach of its corporate network in a recent extortion attack from the Yanluowang ransomware group.
Using a combination of stolen corporate credentials from the Cisco employee’s personal Google account, social engineering, voice phishing, lateral movements, and other tactics, the threat actors successfully accessed corporate Cisco Systems and resources.
As stated by Cisco’s own security teams, the attacker’s escalation of privileges to administrator level allowed them to maneuver inside the network and login successfully to multiple systems. Once in, the Yanluowang group claims to have helped themselves to approx. 2.8GB worth of Cisco corporate data.
Herein lies the critical risk of lateral movements facilitated by unrestrained VPN access. The attackers highlighted yet another fundamental weakness in the “castle-and-moat” traditional VPN method of remote access.
Imagine an organization’s network as a castle and the network perimeter as a moat. Once the drawbridge is lowered and someone crosses it, they have free rein inside the castle grounds. Similarly, if an attacker gains access to the network — that is, if they cross the “moat” — they can also access any data and systems within.

As is evident in this attack, attackers can breach the network by stealing user credentials, exploiting a known access broker, utilizing privilege escalation toolkits, or carrying out a social engineering attack, among other methods. Traditional perimeter protections like Firewalls and other products may thwart some of these attacks, but if one gets through, the cost is undoubtedly high.
Unfortunately, with hybrid workforces blurring lines between personal cloud apps and business apps, organizations – even larger enterprises like Cisco – face unique challenges and heightened risks involving remote access and the volatility that misuse could lead to. Traditionally, your typical hybrid worker would strongly vouch for how critical their VPN remote access. But you can also bet the threat actors are well aware of how valuable remote access is – as demonstrated in this breach of Cisco’s infrastructure.
A Zero Trust architecture applies a secure methodology for how and when users are allowed to access systems and data. Unlike the “castle-and-moat” model, zero trust security assumes that security risks are already present both inside and outside the network. As such, nothing inside the network is implicitly trusted by default — hence the label of “zero trust.”
Zero Trust requires strict assessment and verification for every user and device on the network before granting them access to data and applications. Even then, it gives administrators powerful control over what’s available, accessible, and how the user can interact with resources.
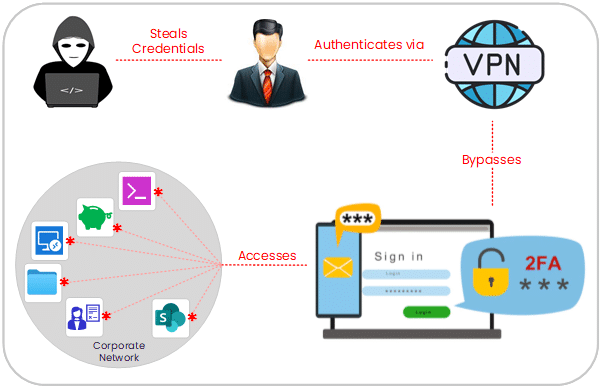
As seen in this attack on Cisco, when attackers use lateral movement effectively, it can be very difficult for security teams to detect. For this exact reason, network segmentation is an essential security process that organizations should implement.
The agility, however, introduced some unintended changes to InfoSec and in order to scale, cloud security cannot be the sole responsibility of one team. Rather, cloud security must be embedded in process and depends on collaboration between development, architects, and operations. These teams now have a more significant role to play in cloud security, and in many cases are the only ones who can implement change in order to enhance security. InfoSec now acts as Sherpas instead of gatekeepers to make sure every team is marching to the same, secure pace.
Using a Zero Trust methodology, security teams can essentially ring-fence their applications and resources, allowing them to create micro-perimeters quickly and efficiently around critical assets.
Our cloud security service was built especially for customers moving and developing applications in the cloud. We call it Skyhigh Cloud-Native Application Protection Platform – or just Skyhigh CNAPP, because every service deserves an acronym.
As data continues to be spread across our cloud infrastructures to enable productivity, organizations must ensure they not only enable content-aware collaboration controls between cloud apps, but also implement cloud Data Loss Prevention capabilities to avoid sacrificing security at the hands of a simple, compromised VPN session.
The sad inevitably of these types of attacks is harrowing. We humans remain to be the weakest links in attacks where social engineering tactics and crafty deceptions are employed by threat actors.
However, as protectors of our IT networks and resources, there is still much that can be achieved through consideration and adoption of modern security principles.
Read the Skyhigh Security Intelligence Digest,
Phishing. Credential Theft. Exfiltration. Extortion. The Saga Continues.
View the entire Skyhigh Security Intelligence Digest series here.
Back to BlogsRelated Content

From the Frontlines: What Fortune 100 CISOs Are Saying About the Future of Cybersecurity
Trending Blogs
From the Frontlines: What Fortune 100 CISOs Are Saying About the Future of Cybersecurity
Thyaga Vasudevan April 3, 2025
Simplifying DPDPA for Indian Enterprises with Skyhigh Security
Sarang Warudkar and Hari Prasad Mariswamy March 13, 2025
Navigating DORA and Key Requirements for Organizations
Sarang Warudkar March 4, 2025
The Hidden Risks of AI Chatbots: When Convenience Comes at a Cost – Skyhigh Security Intelligence Digest
Rodman Ramezanian February 24, 2025
The Evolution of Data Security: From Traditional DLP to DSPM
Hari Prasad Mariswamy February 20, 2025

