Resources
INTELLIGENCE DIGEST
Ticketmaster's Encore: How “ShinyHunters” Hacked the Show
International threat group allegedly responsible for stealing millions of customer records
By Rodman Ramezanian - Enterprise Cloud Security Advisor
July 11, 2024 7 Minute Read
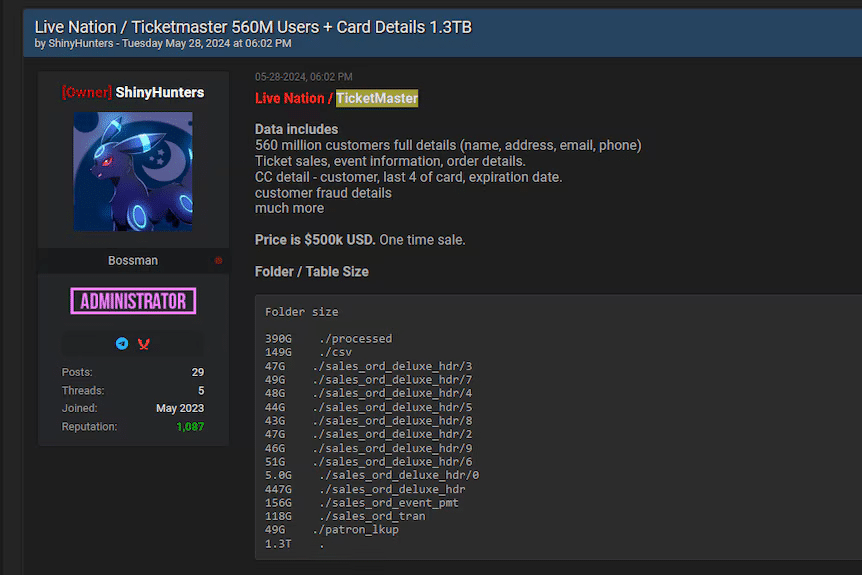
On a clandestine internet forum (another re-emergence of BreachForums), the hacking collective ShinyHunters is currently advertising what they claim to be 1.3 terabytes of Ticketmaster customer data.
ShinyHunters (also known as ShinyCorp) is a global cybercrime syndicate that first surfaced in 2020. This collective has swiftly gained notoriety for executing numerous prominent data intrusions. Despite its whimsical, Pokémon-derived moniker implying a group of innocent hobbyists, ShinyHunters is deeply involved in digital malfeasance, focusing on the exfiltration and monetization of extensive data repositories.
The syndicate’s operations permeate the dark web—an area on the internet that harbors a multitude of unlawful enterprises. This international threat group is purportedly responsible for some of the most significant, high-profile infiltrations of extensive databases in recent times.
Now, they assert possession of the personal information of 560 million Ticketmaster customers worldwide and are offering it for sale at USD $500,000 as a single transaction purchase.
ShinyHunters has garnered a reputation for sophisticated digital intrusion techniques and extensive data breaches. The group’s approach to hacking blends methodical planning with cunning execution, employing a range of strategies to penetrate and exploit vulnerabilities in digital infrastructures.
The typical ShinyHunters modus operandi includes:
- Orchestrating deception campaigns by deploying sophisticated phishing schemes that aim to lure victims with fraudulent emails to capture login credentials.
- Targeting unsecured cloud storage to capitalize on poorly protected online data storage, which is akin to raiding unguarded digital vaults.
- Infiltrating and compromising web platforms and development tools, often purloining login details or application programming interface (API) keys to pilfer valuable data.
- Probing GitHub repositories to scrutinize company code repositories for exploitable flaws, potentially granting unauthorized database access.
- Monetizing via covert networks to profit by trading stolen data on obscure internet marketplaces, catering to buyers seeking illicit information.
Why do these incidents occur?
The attackers allegedly acquired login credentials from a Snowflake employee using information-stealer malware. After gaining access, the attackers created session tokens with the stolen credentials. Subsequently, these tokens were utilized to extract significant volumes of customer data from Snowflake’s systems.
Since the attack, Snowflake has refuted any suggestion of vulnerability or misconfiguration within its platform, asserting that the breach stemmed from compromised customer credentials rather than any security lapse on Snowflake’s part. To make matters worse, the affected account that was breached lacked multi-factor authentication (MFA), which allowed the attackers to log in as if they were a legitimate, trusted user.
According to the Mandiant post-incident report, not only did targeted accounts not have MFA security controls in place, but some of the credentials used in the campaign were compromised a year ago. This underscores the heightened scrutiny focused on specific users, their identities, and corresponding credentials being deemed “trusted” enough to potentially grant unauthorized access, allowing for the devastating theft of hundreds of millions of customer records.
Within most organizations, passwords are still widely used and are likely to continue to be a security mainstay for some time to come. The question is whether passwords can still be used as a trusted method of authentication.
Organizations are increasingly adopting password-less solutions to bolster cybersecurity through a Zero Trust approach, reducing the risk of breaches from credential theft. Relying solely on passwords does not provide necessary identity assurance, posing significant security risks. Prior to transitioning away from passwords, it is crucial to understand the required steps, starting with strong authentication measures. Zero Trust implementation often begins selectively in IT infrastructure and expands gradually, aligning with technology refresh cycles to manage costs efficiently. Embracing Zero Trust and going password-less should be a top priority for enhancing cybersecurity defenses and protecting critical resources more effectively.
What can be done?
The reality is user credentials are the crown jewels of digital security and demand rigorous protection. The 2024 Verizon Data Breach Report points out that human error accounts for 68% of breaches, while misconfigurations and related issues cause one-third. Given these statistics, it is vital to invest in security measures that establish a normal pattern of user activity within your company’s network. This strategy enables security personnel to quickly identify unusual behavior and address potential threats before they evolve into full-scale breaches.
In the current threat environment, it’s not a question of if a breach will occur, but when. When you consider how many high-profile security incidents globally involve breaches of sensitive data, it’s crucial to prioritize investment in a comprehensive data-aware security platform. Moreover, cultivating a security-aware mindset throughout your entire organization is essential. Security is everyone’s responsibility and is not confined to the security team.
MFA is a foundational element of strong security and should be used wherever possible. The Ticketmaster breach serves as yet another example of how valid static credentials (a combination of a username and password) can be compromised and exploited to gain access into a targeted organization’s infrastructure, on premises or in the cloud (as we see here with Snowflake’s cloud-based platform).
The Ticketmaster data breach and related incidents underscore the importance of adopting a Zero Trust architecture. This incident reflects a widespread issue in the industry where organizations are neglecting to integrate SaaS application security into their overall security strategies. Despite the implementation of single sign-on (SSO) and other access management tools, static credentials continue to be in the crosshairs of threat actors, leaving the front door wide open to bad actors who have their eye on an organization’s vital data assets.
Whether a cybercriminal attempts to steal employee credentials or a malicious insider tries to appropriate corporate data, these bad actors typically begin their process by doing what a user does: logging in. That’s why Zero Trust leverages continuous authentication and posture checks, which involves monitoring the user’s (or requesting entity’s) context, status, and activities beyond the initial point of authentication.
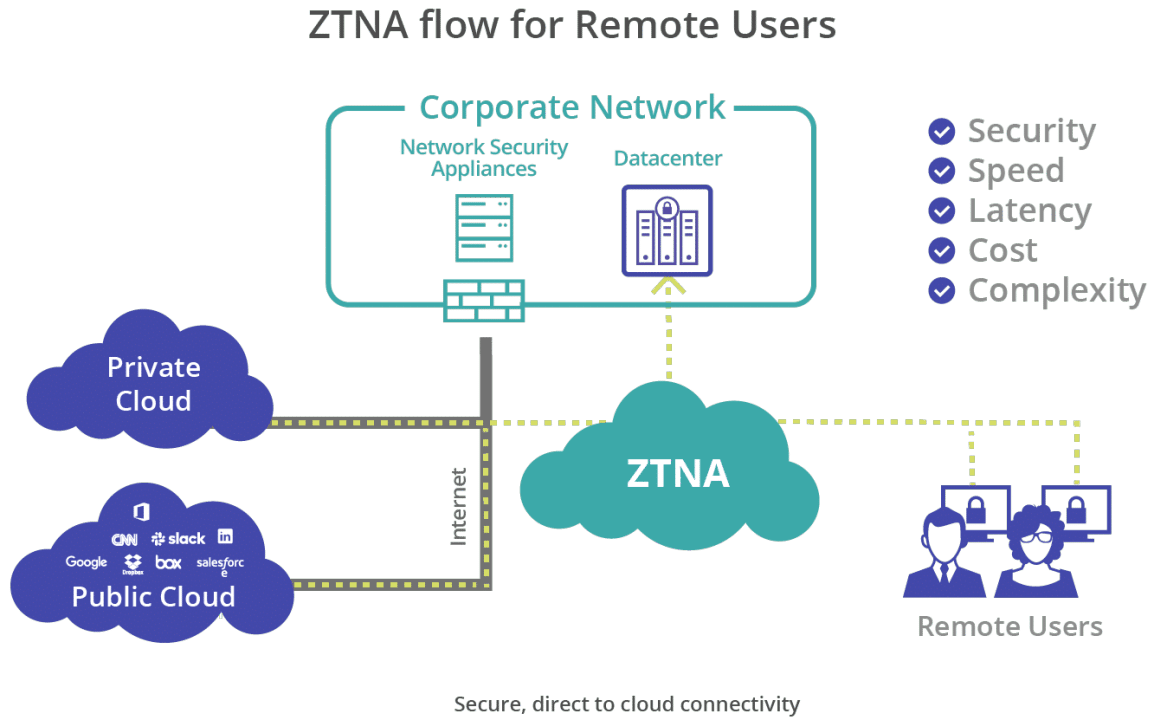
In addition to valid and verified authentication, what other tools or processes are you using to ensure that the data within your cloud applications, services, or platform is being treated and used in accordance with security and data usage policies? This is where convergence of data protections across the web, the cloud, private applications (ZTNA), and devices is critical. Skyhigh Security offers this, along with deep data inspection and classification using inline data loss prevention (DLP) to prevent inappropriate handling of sensitive data while empowering remote users to collaborate from any location and any device. By unifying DLP and threat protection across the most common channels, security teams benefit from end-to-end visibility into and control over sensitive data.
References:
How Skyhigh Security Prevents Data Exfiltration
- Leverage Skyhigh Private Access policies to enforce principles of Zero Trust, controlling verified access directly to private applications, web, and cloud resources.
- Define device profiles and posture assessments for managed and unmanaged devices requesting access to corporate resources, either internally or externally.
- Enable configuration audits to discover misconfigurations before they are exploited and monitor services exposed to unrestricted access.
- Evaluate user activities beyond initial logins to include user movements, behaviors, access to corporate services, locations, and many other potential anomalies.
- Block unmanaged devices, enforce MFA and many other contextual access policies to help stop the abuse and reuse of stolen cloud application credentials.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- The cybercriminal collective known as ShinyHunters has claimed credit for infiltrating Ticketmaster’s systems, asserting that they have exfiltrated sensitive data belonging to 560 million customers.
- The purportedly compromised information encompasses a wide range of personal details, including complete names, email addresses, telephone numbers, residential locations, event-related data, ticket purchase specifics, and order particulars.
- The hacking group further alleges possession of partial credit card information, specifically the final four digits and expiration dates of cards used in transactions.
- The attackers reportedly obtained login credentials of a Snowflake (a cloud data solutions company) employee using information-stealing malware. Once inside, the attackers generated session tokens using the stolen credentials. These tokens were then used to exfiltrate large amounts of customer data from Snowflake’s systems.
- The reported Ticketmaster-Live Nation breach also underscores escalating third-party cyber risks for companies entrusted with customer data.
