Resources
Traditional VPN Replacement using Skyhigh Private Access (ZTNA)
By Saurav Raiguru - Senior Product Manager, Skyhigh Security
May 8, 2024 4 Minute Read

In this blog, we will talk about how organizations can modernize their remote workforce connectivity and access with Skyhigh Private Access, the Zero Trust Network Access solution for traditional VPN replacement. With features such as Network Level Access and UDP, Skyhigh Private Access empowers organizations to retire their traditional VPN, and to step up to data-aware security for private applications.
The modern workforce has been evolving from the beginning of time and it has been our responsibility to evolve along with their growing needs to provide them solutions that are fast and secure. Prior to the pandemic, most of the workforce was working primarily from dedicated offices (on-premise), later evolving to remote work during the pandemic, and now with hybrid being the norm. Hence, the IT landscape had to change to provide seamless, secure, scalable remote access solutions for accessing business applications by workers at any time, anywhere in the world, from any device.
Access has also increasingly shifted from managed to unmanaged, meaning that BYOD devices and unmanaged device support is also required in this IT landscape. However, this level of security and support are not provided by traditional VPNs.
For a work-from-anywhere model, it becomes imperative to migrate applications and workloads to the cloud, since there is a need for:
→ High-speed, low latency data and application access
→ Seamless collaboration amongst workers, partners, vendors, and customers
→ Secure access to business apps hosted in the cloud or corporate data centers
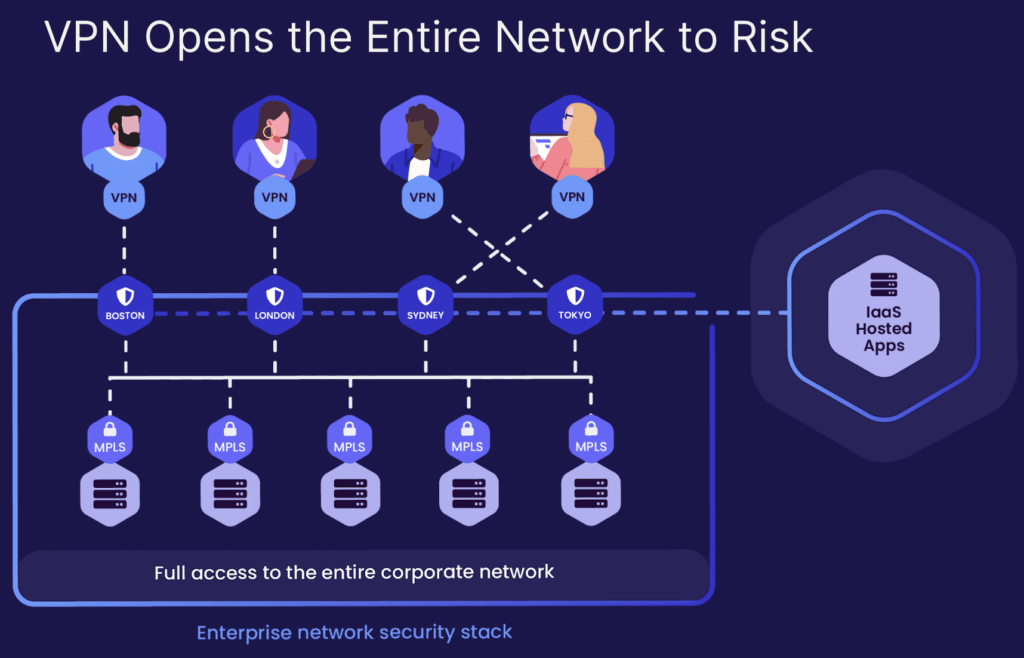
Organizations have used and leaned towards traditional VPN solutions to meet this growing demand from their hybrid workforce. But there are significant challenges that traditional VPNs, such as compliance failures, pose limited and costly scalability, inefficient and slow traffic routings, lower security controls, high cost and complexity of operations.
Traditional VPN use cases are namely remote logins, VOIP, remote troubleshooting, device and printer updates and accessing business apps, to name a few. To meet this growing demand of hybrid workforce challenges, traditional VPNs are not the right choice of technology primarily because they are not scalable in nature, they provide network access to the entire organization which can lead to lateral threat movement, and the infrastructure requires organizations to spend a lot of capital to build and maintain. In addition to latency and cost being inversely proportional, trust in a VPN landscape is also a major factor to worry about, as VPNs rely on implicit trust, thus limiting modern workforce requirements.
In this very scenario, organizations should adopt and move towards Zero Trust Network access (ZTNA) to solve modern workforce needs like remote, hybrid and not traditional VPNs. Zero Trust is a journey and as a principle it moves away from static, network-based perimeters to focus on users, assets and resources. Unlike traditional VPNs that give access to resources at the network-level, Zero Trust believes in providing access at application-level.
The key tenets of ZTNA are to never trust and always verify, remove implicit trust of a VPN, reduce network and capital cost, complexity, prevent lateral threat movement, and offer faster access to applications.
Skyhigh Private Access delivers on these key zero trust principles to provide access to business applications and networks. It supports:
→ Infinite, distributed cloud capacity with 99.99% uptime
→ Unmanaged device coverage supporting mobile, BYOD
→ Anti Malware Scanning
→ Integrated Data Protection with inline DLP Scanning
→ Threat Protection by leveraging isolated browsing sessions on RBI to mitigate risk
→ Posture Check and authentication based on IDP integration, MFA
→ Unified views and actions on a fully converged single platform
Further, Skyhigh Private Access supports flexible combinations of network, application and network + application to enable access at network level adhering to zero trust principles to achieve seamless migration from traditional VPN solutions. To define access to a wide network like a traditional VPN we support apps, networks to be defined as wildcard domains, subnets, IPs, hosts, domains along with their ports / port ranges. In addition to supporting TCP traffic, we also support UDP since most private applications content is increasing and moving towards UDP for traffic steering and management. Organizations can greatly benefit from ZTNA as it solves many challenges faced by traditional VPNs as highlighted earlier like capital, movements, management, scalability etc.
Beyond Network level Access to further make the transition to ZTNA easy, Skyhigh Private Access supports organizations to discover private apps in customer networks. Using Application Discovery, resources can be easily viewed that are accessed by workers (users). Ultimately, discovered private applications can be added as private applications as required by administrators.
ZTNA is the way forward for many reasons as according to Gartner®, “at least 70% of the new remote access deployments will be served mainly by ZTNA instead of VPN services by 2025 – up from less than 10% at the end of 20211.” According to cybersecurity insiders, findings reveal that 90% of the organizations are concerned about third parties serving as a potential backdoor for attackers into their network through VPN access2. According to Gartner®, “the ZTNA market has continued to mature and grow rapidly, forecasting a 87% YoY growth and 51% YoY growth in 2022 and 2023 respectively3”. These statistics clearly show that the future is aggressively moving towards ZTNA solutions rapidly replacing remote access VPNs for application access.
Want to learn more? You can request a demo for more information on Skyhigh Private Access.
Related Content

From the Frontlines: What Fortune 100 CISOs Are Saying About the Future of Cybersecurity
Trending Blogs
From the Frontlines: What Fortune 100 CISOs Are Saying About the Future of Cybersecurity
Thyaga Vasudevan April 3, 2025
Simplifying DPDPA for Indian Enterprises with Skyhigh Security
Sarang Warudkar and Hari Prasad Mariswamy March 13, 2025
Navigating DORA and Key Requirements for Organizations
Sarang Warudkar March 4, 2025
The Hidden Risks of AI Chatbots: When Convenience Comes at a Cost – Skyhigh Security Intelligence Digest
Rodman Ramezanian February 24, 2025
The Evolution of Data Security: From Traditional DLP to DSPM
Hari Prasad Mariswamy February 20, 2025