
Introduction to Data Security Posture Management (DSPM)

As organizations increasingly embrace multi-cloud and hybrid cloud architectures, they are migrating vast volumes of data to the cloud. This expansion of the attack surface has profound implications for their security stance, ushering in new vulnerabilities, reduced visibility, and heightened complexity that result in security gaps.
The move to the cloud or cloud service provider (CSP) architectures, driven by its scalability and cost advantages, unveils extensive data repositories containing sensitive and business-critical data, spread across various clouds, and even residing in unmanaged data stores. “As data is stored, accessed and processed across different CSP architectures that span different geographic jurisdictions, complex data residency, security and privacy risks arise.” (Source: Gartner® Hype Cycle™ for Data Security, 2023).
Leveraging multiple siloed security tools to track, classify and protect data stored in different cloud environments has increased complexity and cost. According to Gartner, “(M)maintaining consistent data security is difficult because so many products provide siloed security tools, use proprietary data classification, act on specific repositories or processing steps, and do not integrate with each other. This restricts organizations’ ability to identify and deploy adequate, and consistent, data security controls while balancing the need to access data throughout its life cycle”.
Gartner, in the Hype Cycle for Data 2023, incorporates several important aspects of data security, including data security governance, privacy and risk, data discovery, categorization and classification of structured and unstructured data, data processing and analytics across endpoint, application or storage layers and more. Gartner mentions it is “important to look for technologies that integrate multiple security controls to simplify orchestration of these controls”.
Definition of DSPM
In the Hype Cycle for Data Security 2023, Gartner defines DSPM as:
“Data security posture management (DSPM) discovers previously unknown data across cloud service providers (CSPs) and categorizes and classifies unstructured and structured data. As data rapidly proliferates, DSPM analyzes data maps and data flows to assess who has access to data to determine the data security posture and exposure to privacy and security risks. DSPM forms the basis of a data risk assessment (DRA) and evaluation of the implementation of data security governance (DSG) policies”.
Gartner in the Hype Cycle for Data Security, 2023, states that DSPM is still in its early stages and DSPM adoption will have transformation benefits for organizations. We believe, DSPM is anticipated to reshape business operations and drive substantial industry-wide changes.
DSPM Objectives and Drivers
The goal of DSPM is to help security teams by proactively identifying, reducing, and remediating cloud data security risks through the analysis of sensitive data by providing visibility, access control, data flow, and the identification of infrastructure vulnerabilities, such as errors and misconfigurations. DSPM is a powerful tool that helps organizations protect their sensitive data from unauthorized access, regardless of where it is stored across their entire multi-cloud, hybrid environments, including unmanaged data stores. DSPM also helps organizations comply with data privacy regulations, such as GDPR and HIPAA. Drivers of DSPM include shadow data, different data formats, increasing regulatory requirements, and cloud vulnerabilities.
In summary, DSPM empowers IT and security teams by enhancing visibility and classifying sensitive data, enforcing least privilege and user activity monitoring, regulating, and overseeing the use of sensitive data as well as proactively mitigating risks and addressing data-related incidents.
- Visibility and classification of sensitive data: Effective data management requires the ability to identify and classify sensitive data across various repositories, including IaaS, PaaS, and DBaaS, even in unmanaged or shadow data stores. This encompasses the discovery of structured and unstructured sensitive data and subsequent categorization based on risk prioritization.
- Least privileged access and user activity monitoring: DSPM provides a comprehensive and accurate view of access privileges for all cloud data repositories and compares them against actual usage to prevent the misuse and exposure of sensitive data.
- Monitor and control of sensitive data usage: Compliance with regulatory requirements such as GDPR, HIPAA, and PCIDSS is a pressing need for many organizations. DSPM facilitates compliance by automating proper controls for sensitive data, ensuring adherence to regulations.
- Proactive risk mitigation and remediation of data-related incidents: DSPM helps security teams minimize the attack surface by proactively identifying, resolving, and sharing best practices to resolve vulnerabilities, such as misconfigurations and errors.
Benefits of DSPM
DSPM gives organizations visibility and control over sensitive data regardless of where it resides, which leads to several benefits, including accelerated detection and response of data-related incidents, proactive risk mitigation of data breaches, reduced risk of insider threats, improved compliance with regulatory requirements, and reduced alert fatigue with fewer false positives. DSPM achieves all of this by identifying risky sharing practices, unauthorized access, inappropriate permissions, and improper data storage – all based on data context.
According to a Gartner® report “Data security posture management (DSPM) solutions are evolving the ability to discover unknown data repositories, and to identify whether the data they contain is exposed to data residency, privacy or data security risks.” Gartner also outlines essential steps for security and risk management leaders to undertake when evaluating and implementing DSPM technologies. This is displayed below.
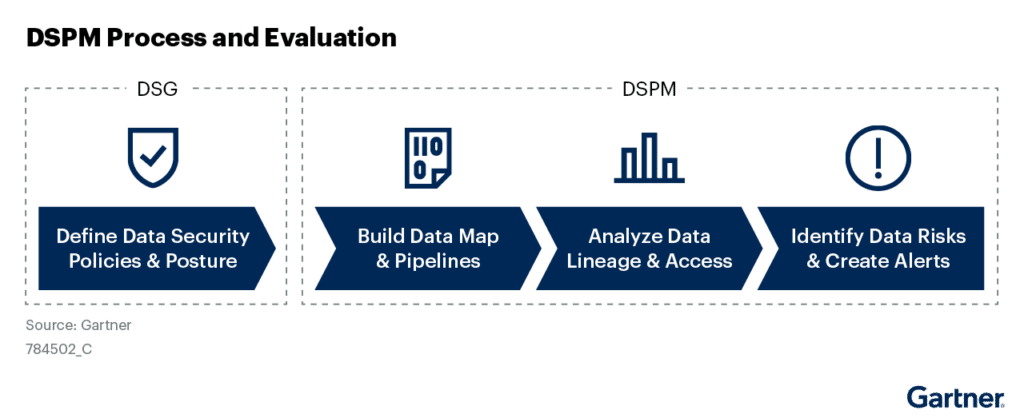
How Skyhigh Security Facilitates Your DSPM Journey
Skyhigh Security’s industry-leading Security Service Edge (SSE) offers a unified Data Loss Protection (DLP) solution, safeguarding your data across web, cloud, email, private apps and endpoints —when accessed from any location, any application and any device. Data and threat protection are performed at every control point, reducing cost and complexity while simplifying management—all from a single converged platform. Skyhigh customers embark on their DSPM journey by:
- Gaining visibility and classifying sensitive data
- Establishing, monitoring, and controlling user activity
- Understanding how data is being used
- Proactively mitigating risk and responding to data-related incidents
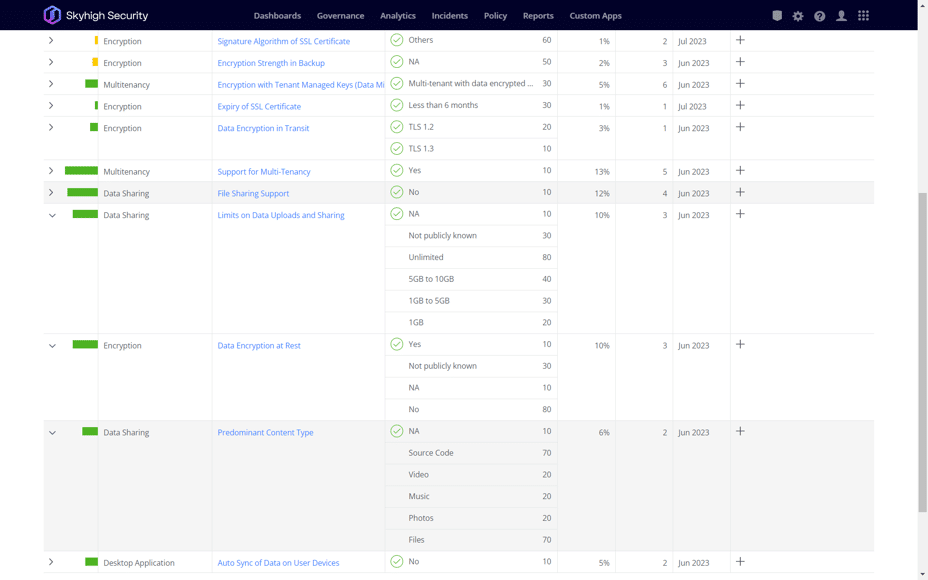
Gaining visibility and classifying sensitive data
With Skyhigh SSE you can discover and identify your sensitive data – whether your data is in use, at rest, or in motion – across cloud, web, private apps, email, and endpoints. You can detect and classify all sensitive data – scattered across multiple clouds, in SaaS apps, private apps, emails or endpoints – in structured and unstructured formats, including images, text, videos, screenshots, and more. Skyhigh Security’s advanced technologies enable you to identify sensitive data, including shadow data, quickly, accurately, and efficiently. Your data is then classified and categorized based on risk prioritization, ensuring protection against unauthorized access and misuse.
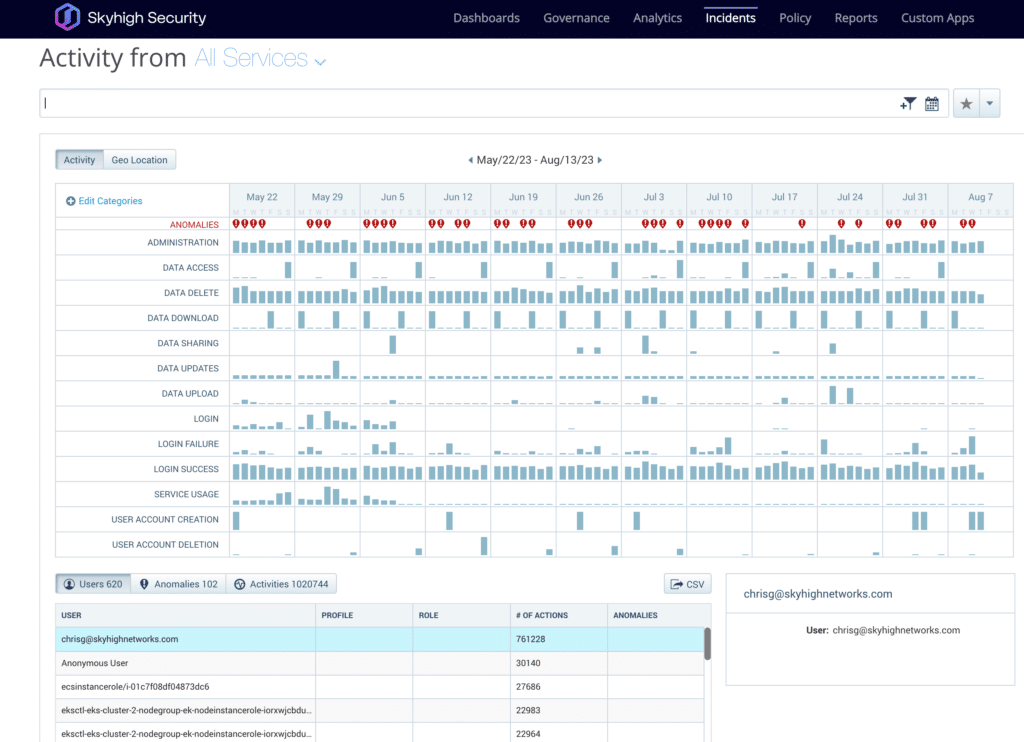
Establishing, monitoring, and controlling user activity
Skyhigh SSE allows you to monitor the activity of your users and detect risky activity across your entire organization, including shadow cloud services. Monitoring and controlling user access to your sensitive data allows you to maintain compliance with regulatory requirements such as GDPR, PCIDSS, HIPAA, and more, while preventing data exfiltration when users access web applications and cloud services. It improves collaboration with internal and external users while ensuring sensitive data does not get exposed.
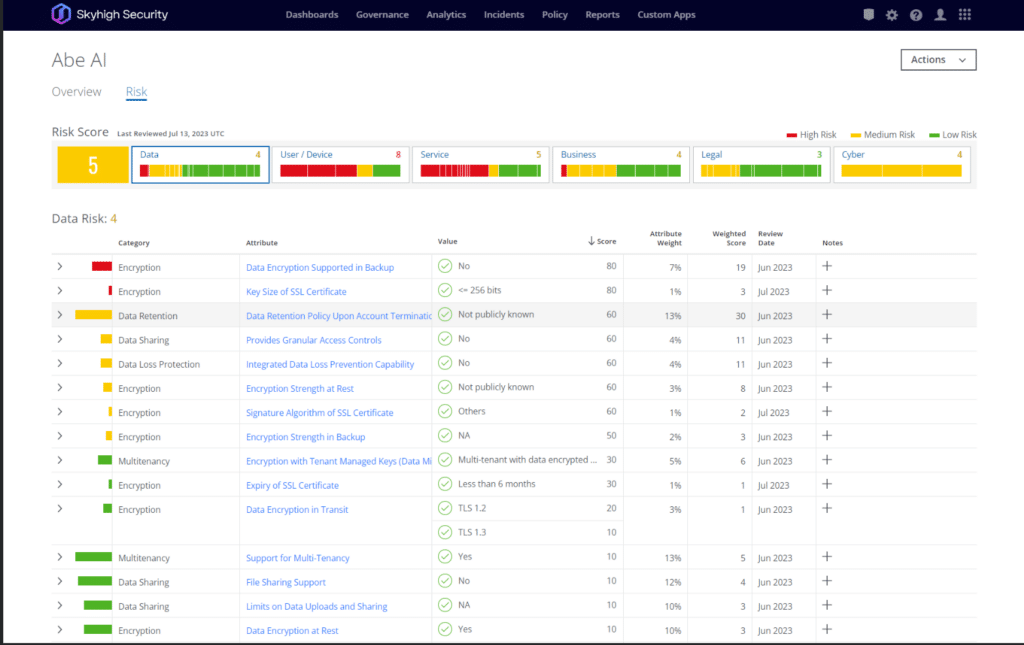
Understanding how data is being used
Beyond visibility into and control over your sensitive data, Skyhigh SSE provides insights into how your data is being used, including what data is being shared, who is sharing this data and with whom. You get insights into the flow of data, including data that is being uploaded to or downloaded from your private applications. We simplify your forensics efforts in identifying data, in the shared responsibilities model with cloud service providers, by narrowing the search in cloud logs and evidence retention sources.
Proactively mitigating risk and responding to data-related incidents
Skyhigh SSE enhances your cloud security posture by providing continuous visibility into your multi-cloud and SaaS environments, automated misconfiguration remediation, and access to a best practices compliance library. Skyhigh gives you consistent data protection across your SaaS, IaaS, and private app environments, identifying hidden risks from misconfigurations, threats, and vulnerabilities, all managed from a unified platform. Skyhigh SSE reduces the number of false positives and prevents the unauthorized sharing of proprietary data by integrating user entity and behavior analytics (UEBA), content screening and information collected from the email processes.
Skyhigh Benefits for Customers
- Skyhigh Security is a SSE leader. We developed the first SSE solution using state of the art technology and focused on protecting sensitive data right from the very beginning. Our SSE platform gives thousands of customers’ employees the flexibility to work from anywhere while protecting business-critical data. We reduce risk, complexity, and cost while delivering advanced data and threat protection.
- Innovation is in our DNA. Innovation is ingrained in our ethos. We’re committed to building innovative data security capabilities, leveraging advanced technologies. DSPM serves as a guide for our future innovation, as we align our data protection offerings with AI, ML, EDM, and IDM technologies, facilitating a seamless transition to DSPM for our customers.
- Comprehensive data protection: Skyhigh Security provides a converged data loss prevention (DLP) solution protecting your web, cloud, private apps, email, and endpoints that gives you granular visibility into how your corporate data is being used, including data at rest, data in use and data in motion.
As an emerging technology, DSPM is still in its early stages. A leader in data-aware SSE, Skyhigh Security is dedicated to building innovative solutions that align with customer and market needs. Contact us to learn more about how we can help you build a solid foundation for your DSPM journey.