Skyhigh Security Solutions
Detect & Mitigate Threats
Understand how users are interacting with corporate data and applications, to easily recognize where the risk is and how to remediate it.

Pervasively capture a comprehensive audit trail of all user and administrator activity to support post-incident investigations and forensics.
Automatically identify attempts and successfully compromised accounts through advanced machine learning-based UEBA.
Discover risks to sensitive data and infrastructure from insider threats by analyzing user behavior in the cloud.
Identify users posing the most risk based on policies, threats and activities.
The Most Powerful Threat Protection
Remote Browser Isolation prevents zero-day threats from reaching endpoints. Skyhigh Security has incorporated RBI technology natively into the Skyhigh Cloud Platform at no extra cost, providing the most powerful form of threat protection available, eliminating the opportunity for malicious code to even touch the end user's device, without impacting the user experience.
Discover RBI
Built-in, Real-Time, Zero-Day Protection
Skyhigh Security’s unique emulation sandboxing technology provides real-time discovery of never-before-seen threats without slow, out-of-band analysis.

Gateway Anti-Malware inspects mobile code in a safe simulation environment, applying patented threat classification technologies to predict potential run-time behavior.
Inline emulation-based sandboxing can prevent zero-day threats in real-time, protecting patient zero without affecting the user experience.
Cloud Access Security Broker Features MITRE ATT&CK
Skyhigh CASB includes MITRE ATT&CK in the workflow for SOC analysts to investigate cloud threats and security managers to defend against future attacks with precision.
Discover CASB Solution Brief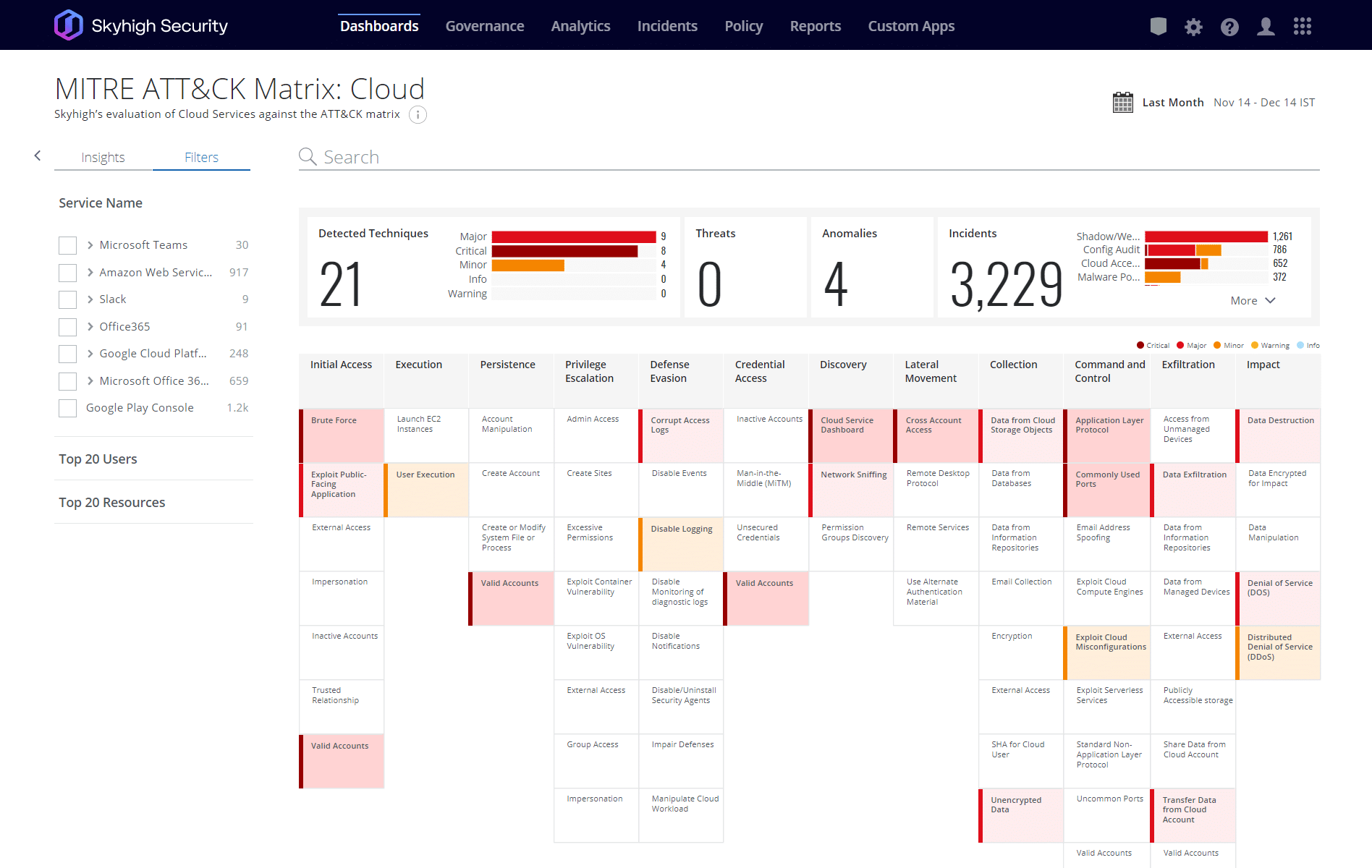
Resources