By Rodman Ramezanian - Enterprise Cloud Security Advisor, Skyhigh Security
June 14, 2022 4 Minute Read

According to a 2020 report by Gartner, 88% of organizations have encouraged or required employees to work from home. And a report from PwC found that corporations have termed the remote work effort, by and large, a success. Many executives are reconfiguring office layouts to cut capacity by half or more, indicating that remote work is here to stay as a part of work life even after we come out of the restrictions placed on us by the pandemic.
Security teams scrambling to keep pace with the work from home changes are grappling with multiple challenges, a key one being how to protect corporate data from exfiltration and maintain compliance in this new work from home paradigm. Employees are working in less secure environments and using multiple applications and communication tools that may not have been permitted within the corporate environment. What if they upload sensitive corporate data to a less than secure cloud service? What if employees use their personal devices to download company email content or Salesforce contacts?
Skyhigh Security Service Edge (SSE) provides enterprises with comprehensive data and threat protection by bringing together its flagship secure web gateway, Cloud Access Security Broker (CASB), and endpoint data loss prevention (DLP) offerings into a single integrated solution. The solution offered by Skyhigh Security features unified data classification and incident management across the network, sanctioned and unsanctioned (Shadow IT) cloud applications, web traffic, and endpoints, thereby covering multiple key exfiltration vectors.
SSE Protects Against Multiple Data Exfiltration Vectors
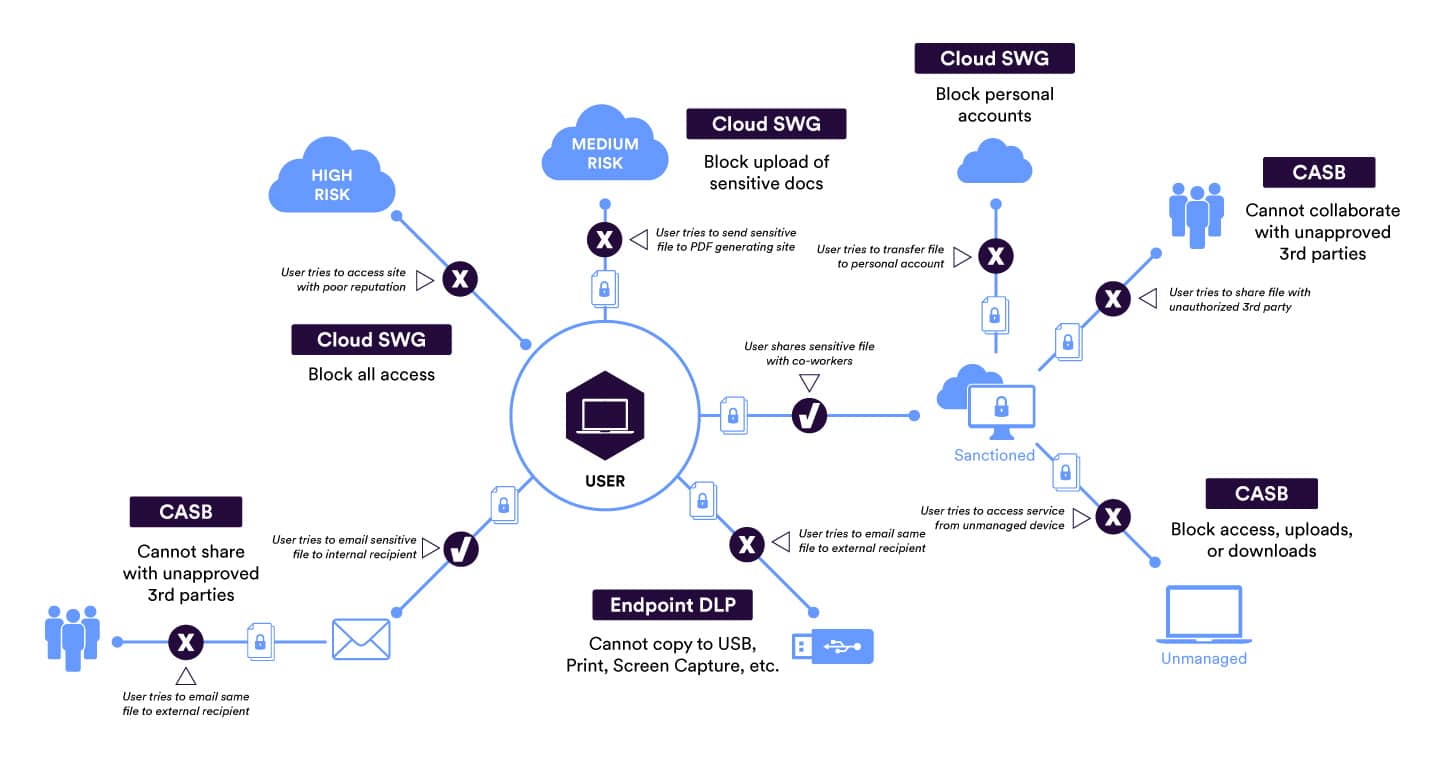
1. Exfiltration to High-Risk Cloud Services
Unfortunately, a wide majority of cloud services do not encrypt data at rest, nor do many cloud services delete data upon account termination, allowing the cloud service to own customer data in perpetuity. Skyhigh SSE detects the usage of risky cloud services using over 75 security attributes and enforces policies, such blocking all services with a risk score over seven, which helps prevent exfiltration of data into high-risk cloud services.
2. Exfiltration to permitted cloud services
Some cloud services, especially the high-risk ones, can be blocked. But there are others which may not be fully sanctioned by IT but fulfill a business need or improve productivity and thus may have to be allowed. To protect data while enabling these services, security teams can enforce partial controls, such as allowing users to download data from these services but blocking uploads. This way, employees remain productive while company data remains protected.
3. Exfiltration from sanctioned cloud services
Digital transformation and cloud-first initiatives have led to significant amounts of data moving to cloud data stores such as Office 365 and G Suite. So, companies are comfortable with sensitive corporate data living in these data stores but are worried about it being exfiltrated to unauthorized users. For example, a file in OneDrive can be shared with an unauthorized external user, or a user can download data from a corporate SharePoint account and then upload it to a personal OneDrive account. Skyhigh Security customers commonly apply collaboration controls to block unauthorized third party sharing and use inline controls like Tenant Restrictions to ensure employees always login with their corporate accounts and not with their personal accounts.
4. Exfiltration from endpoint devices
An important consideration for all security teams, especially given most employees are now working from home, is the plethora of unmanaged devices such as storage drives, printers, and peripherals that data can be exfiltrated into. In addition, services that enable remote working, like Zoom, WebEx, and Dropbox, have desktop apps that enable file sharing and syncing actions that cannot be controlled by network policies because of web socket or certificate pinning considerations. The ability to enforce data protection policies on endpoint devices becomes crucial to protect against data leakage to unauthorized devices and maintain compliance in a WFH world.
5. Exfiltration via email
Outbound email is one of the critical vectors for data loss. The ability to extend and enforce DLP policies to email is an important consideration for security teams. Many enterprises choose to apply inline email controls, while some choose to use the off-band method, which surfaces policy violations in a monitoring mode only.
Skyhigh SSE provides a Comprehensive Data Protection Offering
Using point security solutions for data protection raises multiple challenges. Managing policy workflows in multiple consoles, rewriting policies, and aligning incident information in multiple security products result in operational overhead and coordination challenges that slow down the teams involved and hurt the company’s ability to respond to a security incident. Skyhigh Security brings web, CASB, and endpoint DLP into a converged offering for data protection. By providing a unified experience, Skyhigh SSE increases consistency and efficiencies for security teams in multiple ways.
1. Reusable classifications
A single set of classifications can be reused across different platforms, including Trellix ePO, Skyhigh CASB, and Skyhigh SSE. For example, if a classification is implemented to identify Brazilian driver’s license information to apply DLP policies on endpoint devices, the same classification can be applied in DLP policies on collaboration policies in Office 365 or outgoing emails in Exchange Online. Alternatively, if the endpoint and cloud were secured by two separate products, it would require creating disparate classifications and policies on both platforms and then ensuring the two policies have the same underlying regex rules to keep policy violations consistent. This increases operational complexity and overhead for security teams.
2. Converged incident infrastructure
Customers using Skyhigh SSE have a unified view of cloud, web, and endpoint DLP incidents in a single unified console. This can be extremely helpful in scenarios where a single exfiltration act by an employee is spread across multiple vectors. For example, an employee attempts to share a company document with his personal email address, and then tries to upload it to a shadow service like WeTransfer. When both these attempts don’t work, he uses a USB drive to copy the document from his office laptop. Each of these fires an incident, but when we present a consolidated view of these incidents based on the file, your admins have a unique perspective and a possibly different remediation action as opposed to trying to parse these incidents from separate solutions.
3. Consistent experience
Skyhigh Security’s data protection capabilities provide customers with a consistent experience in creating a DLP policy, whether it is securing sanctioned cloud services, protecting against malware, or preventing data exfiltration to shadow cloud services. Having a familiar workflow makes it easy for multiple teams to create and manage policies and remediate incidents.
As the report from PwC states, the work from home paradigm is likely not going away anytime soon. As enterprises prepare for the new normal, a solution like Skyhigh SSE enables the security transformation they need to gain success in a remote world.
Back to Blogs