Resources
INTELLIGENCE DIGEST
Dropped Out of the Box – Dropbox’s Source Code Repositories Leaked
Phishing campaign leads to unauthorized access of proprietary data
By Rodman Ramezanian - Enterprise Cloud Security Advisor
December 16, 2022 7 Minute Read
The latest inception of phishing attacks is on the horizon. With the pervasiveness of cloud apps and the evolving nature of how they are used, from single-sign-on token integrations, users are being prompted to authorize access in what has become an overlooked attack vector to facilitate data leakage.
The latest inception of phishing attacks is on the horizon. With the pervasiveness of cloud apps and the evolving nature of how they are used, from single-sign-on token integrations, users are being prompted to authorize access in what has become an overlooked attack vector to facilitate data leakage.
Looking back on the year 2022 as it approaches completion, we’ve unfortunately had no shortage of high-profile breaches. Cloud environments continue to be preyed upon at unparalleled rates. Why, you ask? Threat actors view cloud infrastructures as soft targets. And they are continuously refining tactics and tradecraft to exploit the access, vulnerabilities, and misconfigurations within them, ultimately to get their hands on prized possessions. In the case of Dropbox, their “secret sauce” source code was a recent target!
Dropbox is the newest entrant into a growing list of companies such as Uber, Twitch, Samsung, and Nvidia that have had their internal source code repositories targeted and exploited by threat actors.
How did this happen? Sadly, it’s the same old phishing story. Thanks to a crafty phishing email (Figure 1) launched at Dropbox employees, the attackers were able to steal credentials after redirecting users to a fake login page.
Pretending to facilitate integration between their corporate GitHub account and CircleCI’s CI/CD services, the employee would be asked to enter their Dropbox-endorsed GitHub username and password, followed by their hardware-based authentication token to pass through their One Time Password (OTP).
As it turns out, the GitHub account compromised by the attackers belonged to a Dropbox developer. This scored the perpetrators access to approximately 130 internal Dropbox source code repositories stored on GitHub, as well as API keys used by its developers, and a variety of data on Dropbox employees, current and past customers, vendors, and sales leads.
Why do these breaches occur?
As we’ve witnessed in recent attacks, the targeting of internal, privileged users continues to be a hot market for cyber criminals as more valuable data finds it way into the realms of cloud infrastructures.
The nature of this attack involving phishing isn’t exactly novel. Unfortunately, it’s proving impossible for humans to detect every single phishing lure. The reality is that for many people, opening links and attachments is an essential part of their work.
Alarmingly, even the most distrustful, attentive IT expert could fall victim to a meticulously crafted message delivered in the right way at the right time. For this reason, phishing continues to be a vastly successful scheme for attackers. As threats increase in complexity and sophistication, security teams must take heed of appropriate technical controls to limit their organization’s attack surface and protect their prized possessions, namely their highly sensitive, proprietary data.
What can be done?
When talking about threats like phishing, cyber awareness and email safety training are always a wise idea to help employees become more vigilant when faced with devious emails, attachments, links, and the like.
However, sufficient technical controls cannot be discounted due to the high likelihood of users falling victim.
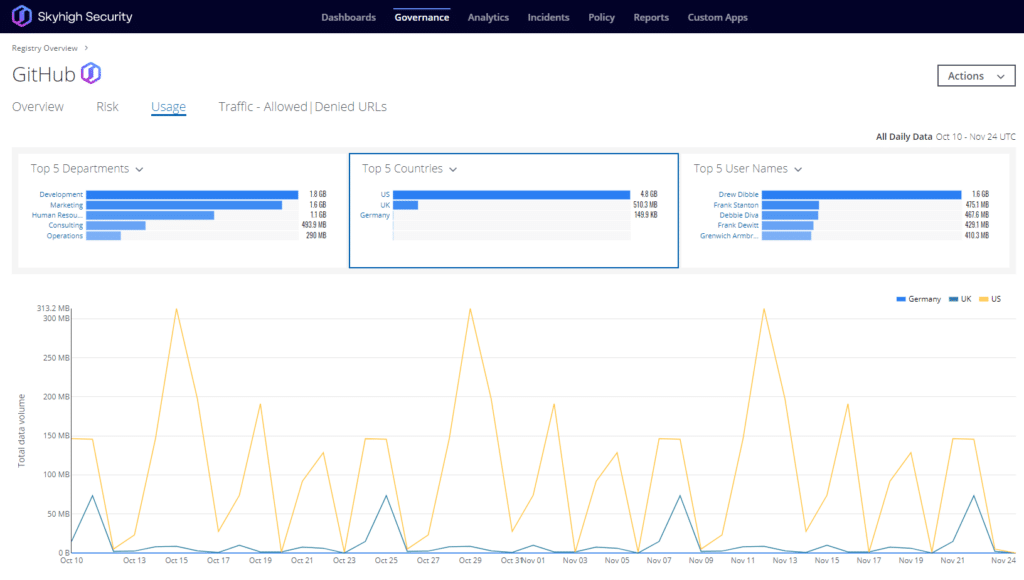
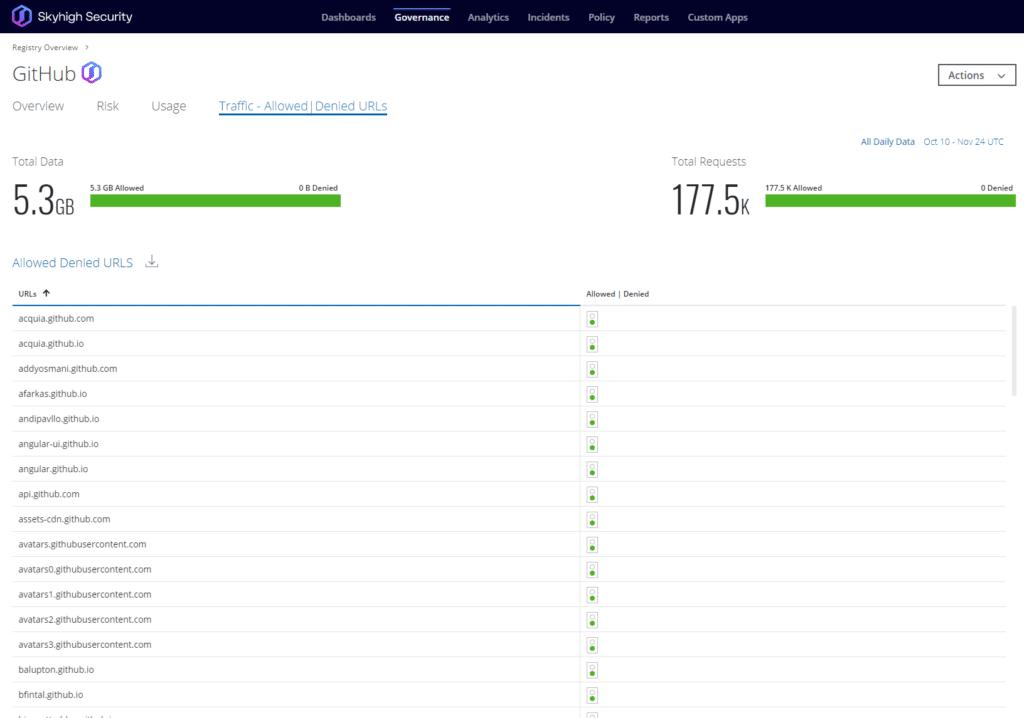
At a bare minimum, security teams must monitor and maintain governance, visibility, and control over the cloud environments – like GitHub – being consumed by their corporate resources. Typically, many teams aim to achieve this by governing access and data leading to and from the cloud service but fall short of implementing and managing consistent security control within the service itself. The reality is that inside these cloud applications and platforms, users – and evidently, attackers – can perform a wide variety of activities that would be deemed “of interest” in the context of keeping the organization’s data and best interests secure.
By allowing security operations administrators to monitor user activity in GitHub, enforce data loss prevention policies, and review User and Entity Behavioral Analytics (UEBA) enriched by machine learning algorithms, security teams can benefit from vastly richer visibility and stronger control, particularly in the case where unauthorized access may have been gained into the corporate GitHub tenancy from a similar phishing attack.
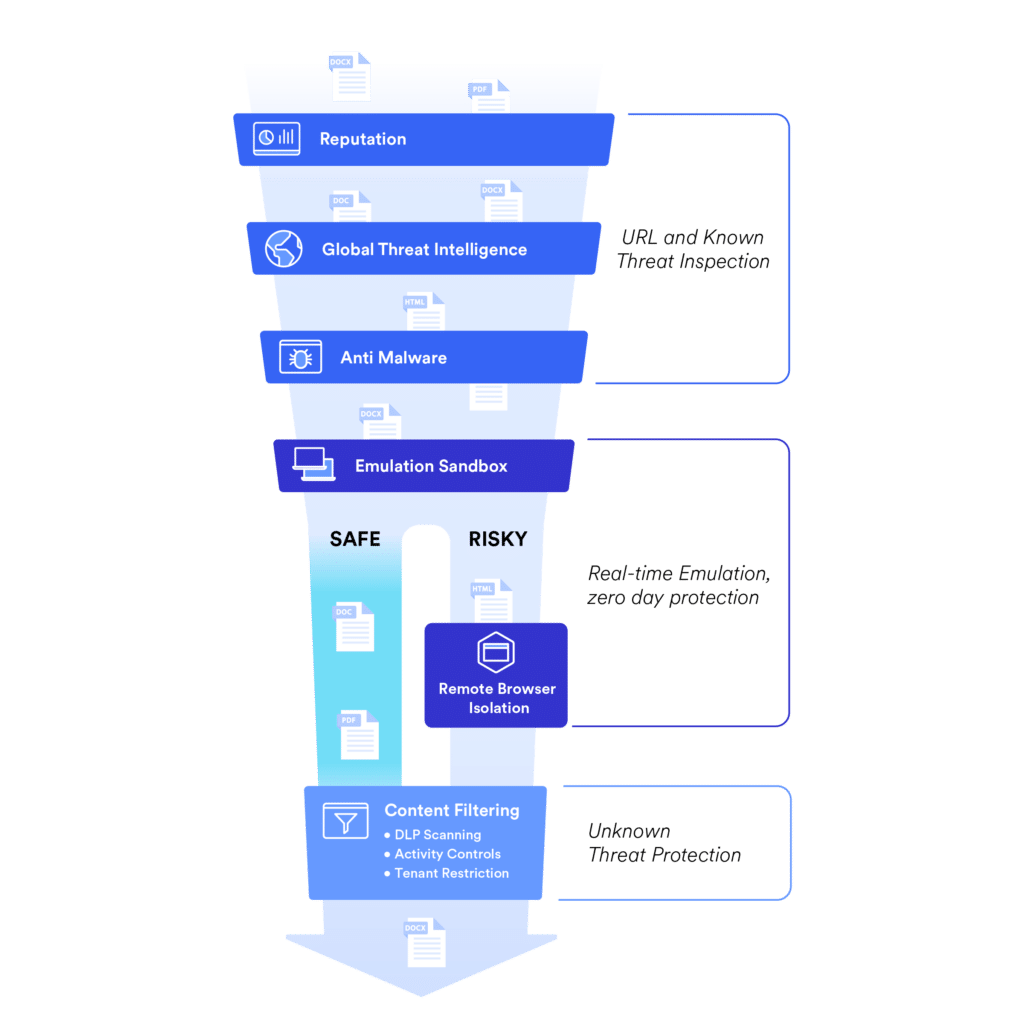
Additionally, in the event of a user mistakenly clicking a phishing link, a capable proxy solution can provide immense value by inspecting the requested web traffic destined to the malicious webpage. In doing so, the proxy solution can immediately detect and protect users from harm, based on the content within the page, the reputation of the web address (especially if its domain has been only recently registered or uncategorized by web reputation engines), and various other attributes.
Here’s how Skyhigh Security picks apart similar content:
Use Skyhigh Security?
- Enable activity monitoring, data loss prevention, and threat protection for GitHub
- Monitor GitHub user activity in the Activity Monitoring page
- Block access to URLs based on reputation and domain categorization
- Enable application of URL information for anti-malware filtering
- Fine-tune URL blocking of phishing links using Global Threat Intelligence
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- The threat actor sent a widespread phishing email imitating CircleCI, a popular CI/CD platform used internally by Dropbox.
- The phishing email took the victim to an imitation CircleCI login page where the user entered their GitHub credentials. CircleCI allowed users to log in with GitHub credentials.
- The imitation site also prompted users to enter a one-time password (OTP), generated by their hardware authentication key.
- The attacker eventually used the OTP and credentials provided by the Dropbox employee to gain access to the victim’s GitHub account.
- The threat actor cloned 130 internal repositories, consisting of both public and private code.
- This attack wasn’t simply just a spray-and-pray phishing campaign that would come from a low-sophistication attack. The fact that the attacker seemingly knew Dropbox used CircleCI and was able to communicate with a hardware key and pass the one-time password to the attacker shows a higher level of sophistication.