By Rodman Ramezanian - Global Cloud Threat Lead, Skyhigh Security
August 26, 2022 4 Minute Read

As is annual tradition now, Verizon recently released their latest “Data Breach Investigations Report” (DBIR), offering highlights and notable insights into targeted industries, the evolving threat landscape we all continue to face daily, and which attack vectors garner the greatest impacts. Think of it as the InfoSec industry’s yearly report card.
This 15th installment of the report opens by recognizing how “extraordinary” the past year has been – particularly, with regards to threats of cybercrime and ransomware in complex supply chain attacks.
The undertone of cloud significance becomes somewhat stronger with each year’s release of the DBIR, and this instalment was no different.
The Human Factor
Akin to previous years, humans remain the number one driver of breaches; 82% of breaches to be exact – either due to compromised credentials, phishing, misuse, or an IT admin misconfiguring their cloud account and accidentally sharing sensitive data with the entire world.
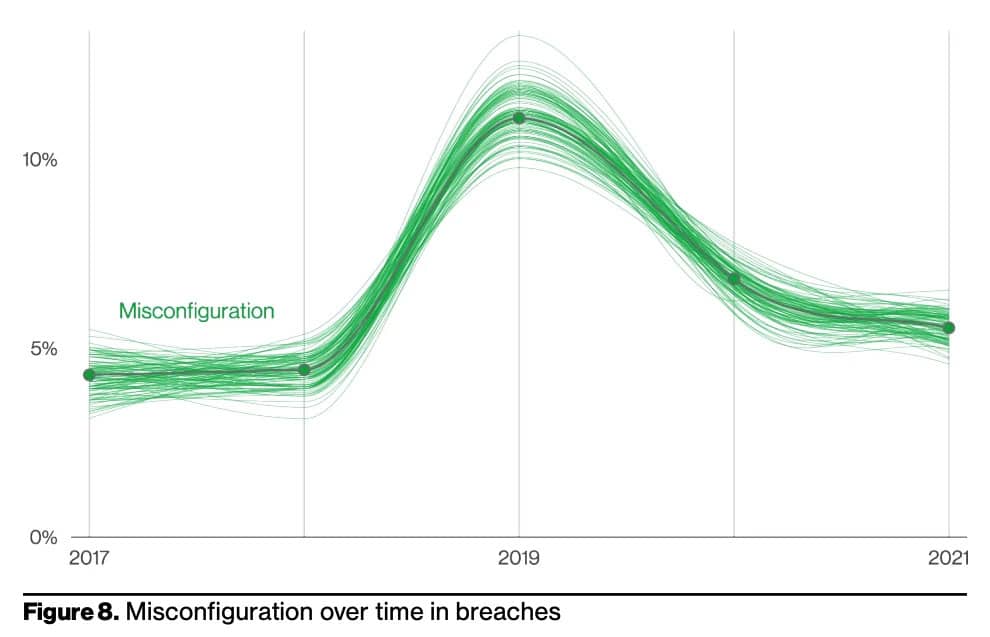 Source
Source: Verizon 2022 Data Breach Investigations Report
According to Verizon, misconfiguration errors continue to be a prevailing cause of breaches, responsible for 13% of breaches over the past year. Notably, misconfiguration of cloud storage was a strong contributor to this. Now, although the graph may suggest a slight decline in more recent years, the misjudgments and tendency of administrators and end-users to err should not be discounted.
Alas, not even the purest of intentions can prevent misconfigurations; leaving enterprises needing a clear method of resolution before they end up on front page of the news.
Fortunately, capabilities like Cloud Security Posture Management are strongly positioned to help remediate and prevent human mistakes and oversights that result in cloud security misconfigurations, blind spots, and weaknesses.
Remote Access Risks
Verizon’s report emphasizes the increasing opportunities that remote access offers attackers in their plans to exploit vulnerabilities and exposures.
Remote access software and the widely-familiar Remote Desktop Protocol (RDP) were underscored as top threat vectors. The harsh reality is that if users can directly reach their devices over the open internet using nothing but credentials, so too can the threat actors. Alarmingly, remote desktop sharing software contributed to 40% of ransomware incidents that were evaluated.
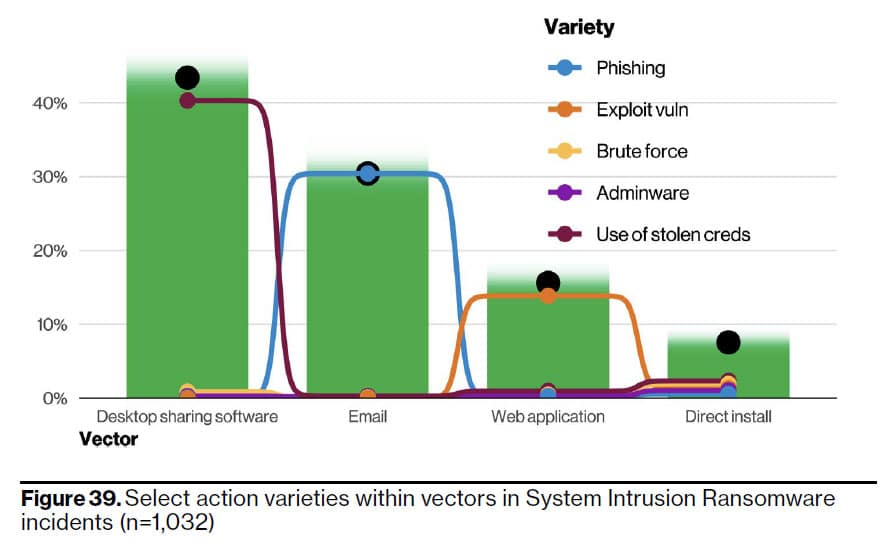 Source
Source: Verizon 2022 Data Breach Investigations Report
As almost anyone will attest to, remote access to systems, applications, and data has kept us all operational and productive over the past 24 months. Rather than committing to impractical aims of reducing remote work, limit access permissions by adopting a Zero Trust Network Access architecture. By keeping access restricted to only approved apps and services from authorized users on posture-assessed devices, while importantly protecting data within those resources, you can keep an attacker who has compromised an identity (or obtained credentials) from reaching too deeply into your organization’s assets.
The Insider
Organizations are continuously concerned about the nefarious insider(s) that may turn against them at any moment. It’s a profoundly unnerving feeling to think that someone you work with could be planning to cause harm from within.
An organization is almost four times more likely to be attacked by an external actor than a privileged insider. But take that with caution, as it shouldn’t discount the devastating force of insider attacks. It’s worth remembering that not all insider jobs are publicly reported or even undetected.
Particularly startling is the fact that insider breaches are the most destructive from a records exposure perspective, resulting in 10 times more compromised records being exposed than external breaches do. As you can imagine, the more access that the insider has, the more damage they can do.
With privilege misuse being the key contributing threat vector, it reinforces the importance of adopting Zero Trust Network Access methodologies. By denying access to any resource by default, and enforcing identity-aware, adaptive controls based on posture, context, and risk, impacts of privileged account misuse can be significantly reduced.
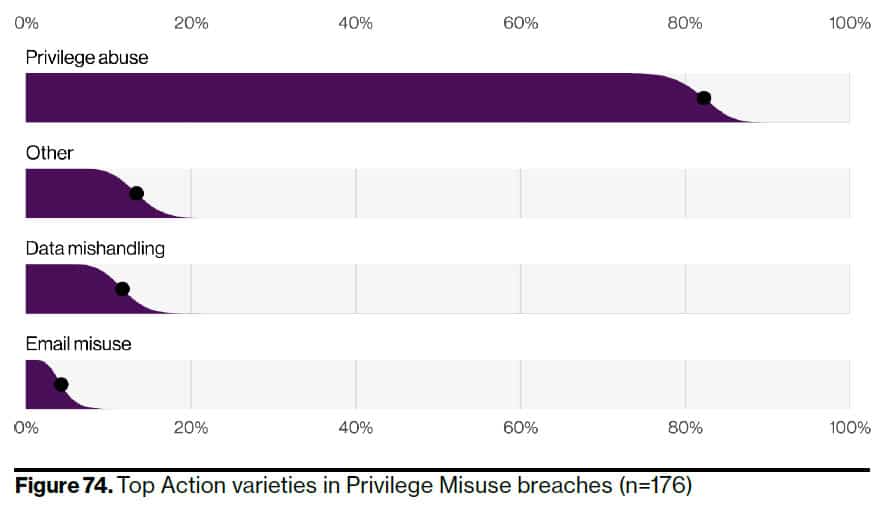 Source
Source: Verizon 2022 Data Breach Investigations Report
Source:
https://www.verizon.com/business/resources/reports/dbir/2022/master-guide/
Wrapping Up
Here are some “quick wins” to take advantage of:
- Increase Visibility across your web and cloud movements.
- If you can’t see it, you can’t protect it.
- Enable Posture Management to maintain a strong foundation.
- Don’t fall victim to the “low hanging fruits” attackers leverage.
- Protect your data wherever it goes.
- Data has no jurisdiction, so neither should your defenses.
As the threat landscape continues to shift faster into the cloud universe, it should be no surprise that the risks of yesterday may not be the same today. Tactics, techniques, procedures, and unfortunately, even honest user mistakes will become more cloud-centric as the world continues to embrace the paradigm of cloud computing.
However, as defenders of our assets, networks, and organizations, there’s much that can be done to set stronger foundations and minimize those risks to the lowest possible thresholds. Have a chat to us at Skyhigh Security about how we can help along that journey.
Request a demo today!
Back to Blogs