By Tony Frum - Product Specialist, Skyhigh Security
July 20, 2022 7 Minute Read

In today’s reality of heavy cloud usage both for personal and business purposes, web security has become of paramount concern yet extremely complicated. Diverse network architectures, remote users, a plethora of client platforms, bring your own device (BYOD), the waning of the traditional network perimeter, and countless other technical considerations challenge security professionals who attempt to secure their organization’s web traffic.
DNS security has emerged as an alternative to a full-blown secure web gateway (SWG) solution promising simplicity and speedy deployments. Essentially, DNS security plugs into domain name resolution to prevent access to risky domains. This allows organizations to streamline web security by treating domains as “neighborhoods.” It prevents access to riskier domains and steers users toward more secure areas. While this approach greatly simplifies the web security problem, it comes with some limitations. Let’s take a close look at what makes DNS security so attractive and analyze whether it’s truly the silver bullet many organizations are looking for.
Is DNS security enough?
The benefits of DNS security are clear. Its most appealing feature is that there is no need for network rearchitecting. The network team’s involvement is typically minimal. DNS security also enables organizations to extend protection to the network effortlessly to secure an ever-growing number of offsite users. As an added bonus, DNS security goes beyond the capabilities of SWG by providing coverage for all ports and protocols. Policy enforcement is simple. You can block high-risk domains and potentially malicious web categories. Taking all these benefits into account, DNS security seems like a logical choice.
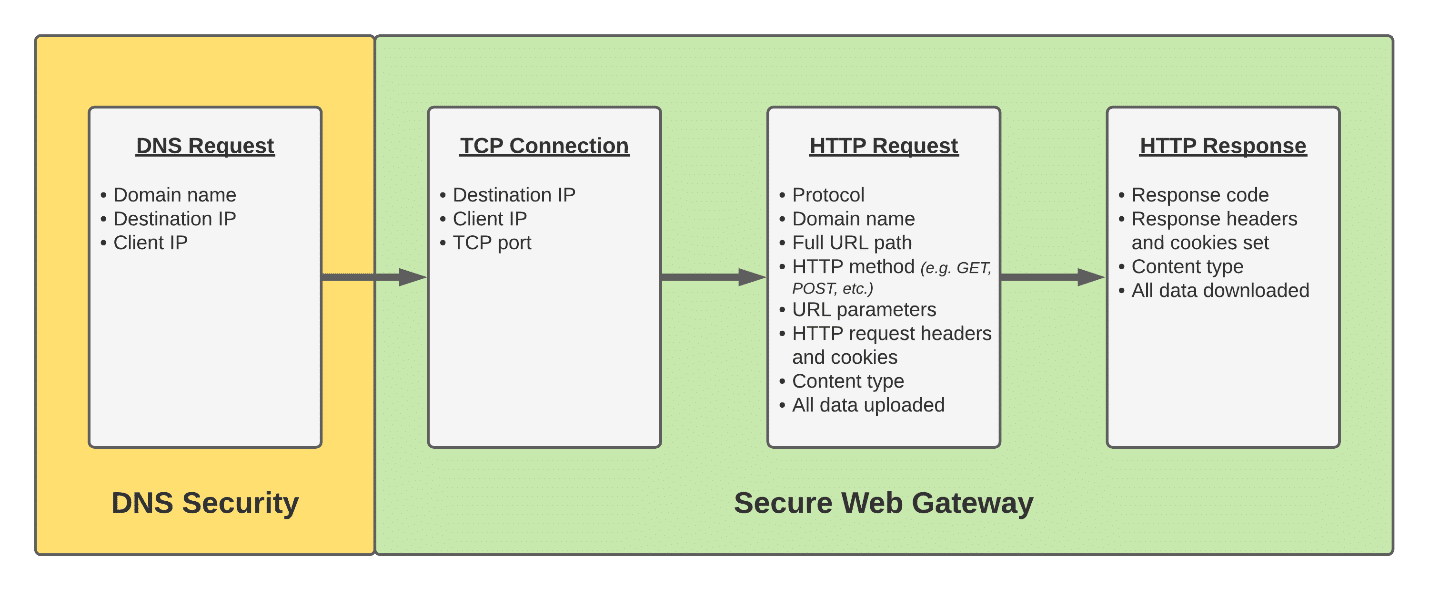
But all this goodness comes at a cost. In a word, visibility. When you relegate your web security to looking at DNS requests, you lose important context and acuity. A DNS security solution knows that a domain was resolved by a client. But relevant information about the traffic sent to the domain after DNS resolution is unknown. Your DNS security solution cannot answer these questions: “How much traffic was sent to or received from this domain? What protocols were used and on what ports? What files were transmitted, and were they malicious? Was any sensitive data uploaded to personal cloud accounts?” These unanswered questions underscore the lack of visibility and context and expose glaring security gaps in DNS security.
Let’s consider a worst-case scenario. What if your organization were targeted with web-based threats? How hard would it be for an attacker to circumvent your DNS security entirely? One option would be to get malicious content onto a “known good” domain. This could be as trivial as a shared link to a file on a personal Dropbox or OneDrive account. An attacker could also simply avoid using domain names altogether. Using a URL with an IP address in a phishing email is probably just as likely to trick a gullible user as a link using a hostname. Even if the attacker needed to use IPs dynamically, there are other ways to get an IP to a victim machine, such as posting to a social media account, dropping it into an Amazon S3 bucket, or countless other options. You simply cannot assume that DNS queries will be a part of every attack on your environment.
In addition to visibility, control is also sacrificed in the name of simplicity and fast deployment. When your control point is limited to a DNS request, your response options are limited as well. Often, you’re left with the option to allow or block, and this decision has to be made with no more context than a domain name. This results in either an overly lenient and risky policy or a more severe alternative that will cause users to perceive the security team in a negative light. There is no option to implement a more practical policy such as, “Facebook is allowed, but you can’t chat” or “Personal Dropbox accounts are allowed, but uploads of sensitive data are scanned.”
Why SWG is a better, more comprehensive alternative
With this in mind, it’s apparent that SWG brings multiple benefits to the table. It’s a highly mature technology purpose-built to decipher and scrutinize the one protocol that probably accounts for more than 90% of traffic generated by your endpoints: HTTP/S. SWG offers visibility and context that are not available with DNS security. Domain names are shown as full URLs. You can scrutinize the content of every single request, including both traffic sent and received by endpoints.
This increased visibility translates directly into improved security. SWG solutions not only ensure that users are visiting appropriate and trusted domains, it also performs malware analysis on all downloaded content, including a link to a file from a personal Dropbox account. When content is uploaded, it can be scanned for sensitive data to ensure no regulations are broken or intellectual property lost.
A more recent addition to the SWG toolkit includes the ability to enforce tenant restrictions. Tenant restrictions are a critical way to ensure data protection by only allowing users to access sanctioned services with a sanctioned tenant (or an instance) within those services. Coupled with cloud access security broker (CASB) controls, enforcing tenant restrictions allows data to safely migrate “out the door” through the web security solution while still remaining within the organization’s control. Because API-based CASB controls can only be applied to tenants owned by the organization, prohibiting users from using “shadow” tenants is critical.
Deep inspection of all web traffic also empowers organizations to apply more tactical responses to certain user behaviors. This is not possible with DNS security. For example, with SWG, activity controls are a common capability that allow security teams to permit domains related to some cloud applications but prevent certain activities within those applications. Users want access to their personal Dropbox or Evernote accounts, but security teams are concerned about data security. Using activity controls, you can permit these applications but prevent uploads.
Another example is user coaching. Let’s say an allowed domain has been compromised. Rather than react by blocking the domain, the organization can decide to notify users and require them to change their credentials immediately.
Another fairly recent advancement allows content with unknown or only slightly suspicious risk to be viewed through an isolated browser. Remote browser isolation (RBI) allows users to access content not known to be safe while still insulating endpoints from risk. The requested content is loaded into a temporary browser that is isolated in the web security vendor’s data center. The user is allowed to view and interact with that remote browser without loading any of the site’s content locally. This allows access to the content while preventing any malware risk on the endpoint.
How easy is it to deploy SWG?
The final goal is the use of cloud native deployment instead of on-premise solutions. But, as mentioned previously, in many cases the path there can be made bumpy by the rip-and-replace approach, or it can be made smooth by phasing out on-premise equipment with a synergistic solution optimized to enable the transformation while minimizing disruption.
While organizations have much more to consider when deploying SWG solutions than DNS security, the industry has come a long way toward simplifying the approach of this technology. The days of racking and stacking servers in data centers across the world are over, as many SWG vendors do the legwork for you. SWG solutions are delivered using cloud-native infrastructures that offer a global footprint, with performance and reliability rivaling what even the largest organizations would likely achieve. Network and security teams no longer have to find ways to backhaul traffic from smaller sites to a central location for filtering, as site-to-site VPN capabilities allow the direct use of the SWG vendor’s infrastructure. Likewise, remote users, do not have to rely on VPN for their protection—intelligent agents ensure their traffic is protected using on-premises or cloud assets where appropriate.
SWG technology has also dramatically simplified web security policy. Gone are the days of defining lists of URLs or IP ranges that need to be allowed or blocked. Web policy is enforced at the cloud application level rather than the domain and activity level rather than the URL. Out-of-the-box policies allow security teams to achieve all their desired outcomes in minutes, without having to settle for rudimentary control or resort to complicated configurations.
The best of both worlds
Despite common perception, SWG and DNS security technologies are not competing technologies, but rather complementary solutions. Looking at the two offerings from a visibility point of view, you’ll find the overlap is fairly minimal.
DNS security can be described as a mile wide and an inch deep. The breadth of visibility is clear, as all ports and protocols are covered, but there is little depth, since DNS security works solely with a domain name.
SWG, on the other hand, is a mile deep and an inch wide. Generally, a small set of critical protocols are supported, but inspection goes to the deepest levels of web traffic.
A CISO of a medium-size organization just starting to tackle the problem of security might start with DNS security as a “quick win” and then advance to an SWG solution to achieve truly comprehensive web security.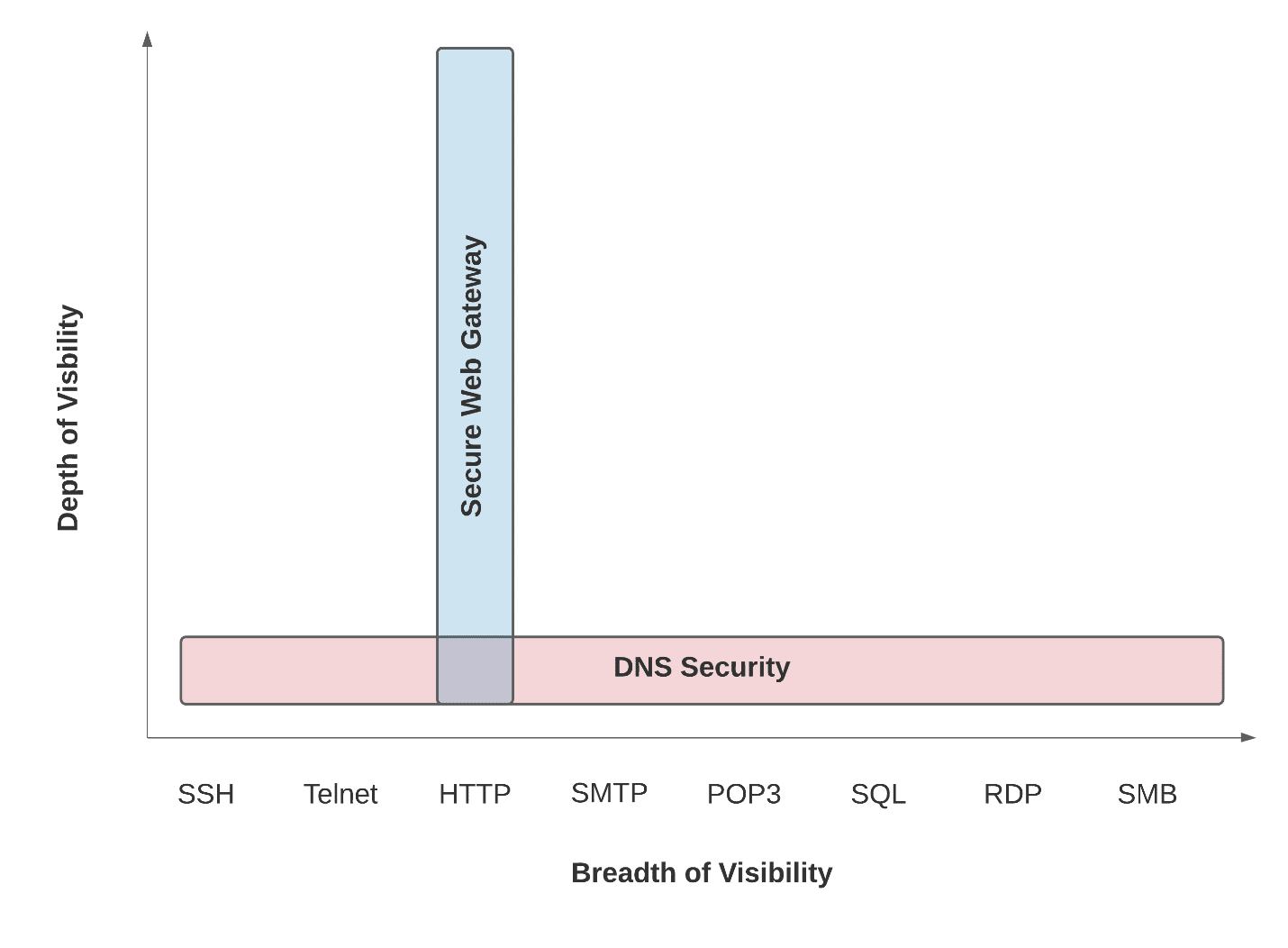
Closing web security gaps with SWG
DNS security alone does not constitute true web security. There are simply too many gaps in visibility, rendering security and reporting insufficient. There is no malware scanning of downloaded content or data security for uploaded content. There is minimal context to answer questions about what actually happened between this domain and your endpoints.
SWG technology, on the other hand, has advanced throughout the decades to achieve the security goals of the world’s largest organizations, despite the complexity of a cloud-first world. SWG provides deep inspection of all web traffic, along with powerful anti-malware and data security technologies to ensure that information and endpoint assets are protected against a variety of threats. Reporting and visibility offer rich detail and context into all interactions with cloud-based applications. And, best of all, DNS security and SWG pair up to offer a best-of-both-worlds approach to secure any organization from today’s threats.
Learn more about Skyhigh Security Secure Web Gateway by clicking here.
Sign up for a live demo here.
Back to Blogs