An unsecured server has exposed sensitive data belonging to airport employees across Colombia and Peru. The AWS S3 buckets containing approximately 3TB of data dating back to 2018 consisted of airport employee records, ID card photos, and personally identifiable information (PII), including names, photos, occupations, and national ID numbers.
Airport security protects the lives of travelers and airport staff. As such, this breach, which was discovered by SafetyDetectives, is extremely dangerous with potentially devastating consequences should the bucket’s content end up in the wrong hands. Within Colombia, Peru, and around the world, guerrilla criminals and terrorist organizations now pose a serious threat if they were to access this unsecured AWS S3 bucket.
Sadly, such types of breaches and incidents are not novel or unique as organizations stumble in the cloud.
Part of the problem is the unanticipated speed with which many organizations have undertaken their cloud adoption process, in a desperate scramble to provision their employees to work remotely as a result of the COVID-19 pandemic. As expected, threat actors and APT groups, relish these prospects.
 Figure 1. Number of Non-Compliant IaaS resources deployed in AWS: Skyhigh Security.
Figure 1. Number of Non-Compliant IaaS resources deployed in AWS: Skyhigh Security.
How did these breaches occur?
Most organizations that fail to control public cloud use will inappropriately share sensitive data. Unfortunately, news headlines like these highlight examples of a data breach due to a simple, but harmful misconfiguration: an unsecured, exposed cloud storage service. Complexities around identity management, access permissions, secure configurations, data protection, and so much more, continuously result in poor cloud security hygiene and ultimately, data exposures.
What can be done?
Ideally, tightening read/write permissions may be the first and only reactions that come to mind. In reality, it will take far more than that; thanks to the extensive manners by which cloud storages can be accessed and misused. Skyhigh Security addresses these challenges and minimizes associated risks by applying a number of fundamental capabilities, thanks to tight integrations into many cloud platforms.
As global breaches continue to arise at the hands of ransomware attacks and criminal actors, Skyhigh Security’s cloud security posture management, vulnerability assessments, configuration audits, and data protection capabilities aid organizations by continuously applying optimal security while reducing complexities related to managing storage across multi-cloud environments.
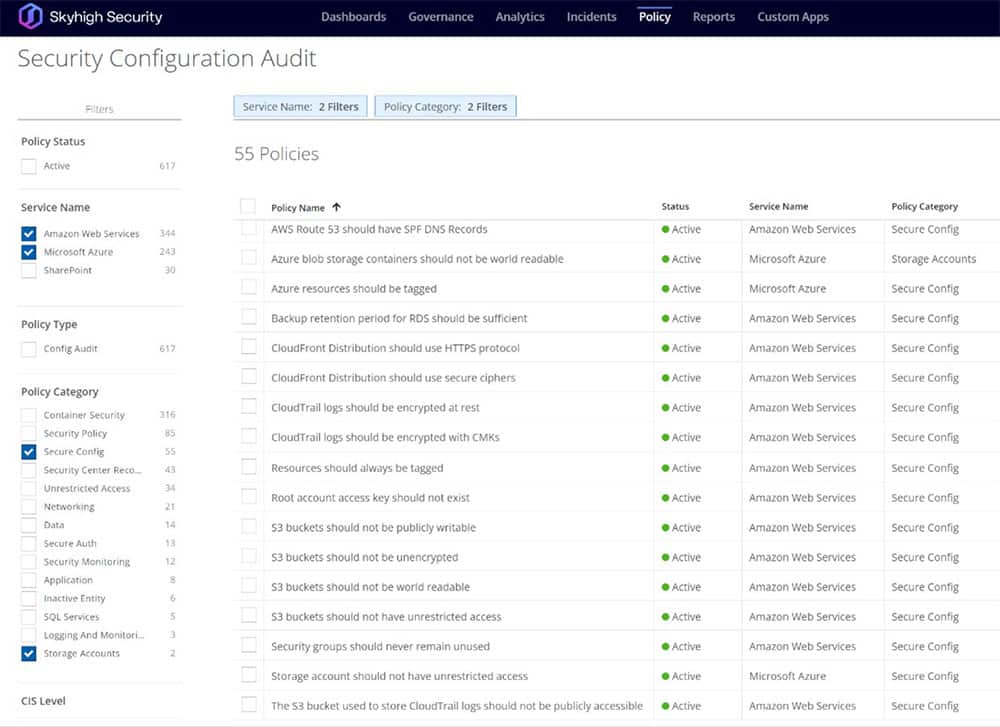 Figure 2. Skyhigh Security Configuration Audits for Cloud Services (filtered results).
Figure 2. Skyhigh Security Configuration Audits for Cloud Services (filtered results).