Resources
INTELLIGENCE DIGEST
Healthcare Havoc: Data Breach Strikes Dozens of Hospitals and Clinics
Healthcare industry rocked by massive data breach impacting millions of victims
By Rodman Ramezanian - Global Cloud Threat Lead
August 16, 2023 7 Minute Read
HCA Healthcare, a prominent healthcare provider with a widespread presence in Florida and 19 other states, recently fell victim to a severe data breach potentially affecting as many as 11 million people. The unsettling incident came to light when personal patient information surfaced on an online forum.
Specifically, the breached dataset included sensitive Personally Identifying Information (PII), comprising:
- Names, cities, states, and zip codes of patients
- Contact details such as telephone numbers and email addresses, along with gender and dates of birth
- Specific service dates, locations, and upcoming appointment dates
According to HCA’s statement, the threat actors stole 27 million rows of data from an “external storage location” but it had not detected “any malicious activity” on HCA’s networks or systems.
With the average cost of a healthcare data breach rising to $11 million, according to IBM Security’s 2023 Cost of a Data Breach Report, it serves as a stark reminder of the ever-growing importance of robust cybersecurity practices in the healthcare industry.
The health industry encounters a higher number of data breaches compared to all other sectors, as consistently reported by the Ponemon Institute and Verizon Data Breach Investigations Reports.
Why do these incidents occur?
In this instance, the unauthorized access of an “external storage location” facilitated the vast data theft. Traditionally, storage locations would be heavily guarded by internal Data Loss Prevention controls or Database Activity Monitoring technologies buried inside internal infrastructures.
Unfortunately, however, the reality of modern-day business and IT operations involve a diverse variety of users, devices, locations, contexts, and business purposes to interface with that stored data. These variables present unique challenges to how data needs to be protected; especially in the case of accessing “external storage locations” outside the traditional network perimeter.
Given the interconnected nature of healthcare systems, the compromise of a single target can result in far-reaching implications.
According to the Center for Internet Security (CIS), “Personal Health Information (PHI) is more valuable on the black market than credit card credentials or regular Personally Identifiable Information (PII). Therefore, there is a higher incentive for cybercriminals to target medical databases.”
Constantly looming as a serious menace, cyberattacks pose significant risk to organizations, encompassing potential harm to business operations, intellectual property, sensitive data, and reputation. However, in the healthcare domain, the stakes are raised even higher. The loss of data can lead to life-threatening consequences, while the theft of patient records constitutes a breach of privacy with enduring impacts on the affected individuals.
The healthcare sector, in particular, grapples with a number of cybersecurity challenges:
- Inadequate investment in secure digital infrastructures
- Insufficient training
- Outdated and vulnerable infrastructures
- Subpar cybersecurity practices
- Complexities arising from multi-agency dependencies
- High costs associated with cybersecurity implementation
- A lack of cyber literacy among the workforce
The accumulation of these issues creates numerous vulnerabilities and inadequately protected entry points that are ripe for exploitation by threat actors. When these weaknesses are relied on to protect highly sensitive and valuable data, the potential consequences become immense, leading to extensive damage.
What can be done?
Unfortunately, these data breaches are outside the control of the average person. Healthcare providers typically use the information they collect from you for your treatment, so you cannot withhold certain details from hospitals and healthcare providers.
In the modern era of interconnected networks – such as those used by hospitals and healthcare providers- organizations often rely on external storage locations, such as third-party data centers, outsourced data warehousing solutions, or cloud storage providers, to store and manage their data. While these external storage solutions offer convenience, scalability, and cost-effectiveness, they also introduce significant security risks. This is where the concept of Zero Trust Network Access (ZTNA) comes into play.
ZTNA treats every request (take: an access request to an external storage location, for example) as potentially malicious and requires verification and authorization at every step of the process. This is especially crucial when dealing with external storage locations for the following reasons:
- Data Exposure and Leakage: External storage locations, especially cloud storage services, may be accessed by numerous parties, including a service provider’s employees and other users. Without proper security measures, sensitive data might be inadvertently exposed, leaked, or accessed by unauthorized individuals.
- Credential Compromise: If an attacker gains access to valid credentials through phishing, social engineering, or other means, they could exploit these credentials to access the external storage location and the data within. ZTNA minimizes the impact of compromised credentials by requiring additional authentication factors and continuously re-evaluating the requesting party’s trust level.
- Insider Threats: While organizations trust their employees, insider threats remain a possibility. Employees with legitimate access to external storage locations might misuse their privileges or fall victim to credential theft, leading to potential data breaches. ZTNA mitigates this risk by constantly assessing user posture, context, and behavior.
- Lateral Movement: If an attacker successfully infiltrates an organization’s network, they might attempt to move laterally and gain access to storage locations – either internally or connected externally. ZTNA restricts opportunities for lateral movement, reducing the attack surface and limiting potential damage.
- Integrated Data Protection: Embedded Data Loss Prevention (DLP) capabilities prevent unauthorized users from uploading, downloading, and even viewing sensitive data from any location or device. Adaptive access controls can be enforced based on continuous device posture assessments.
When it comes to the protection of any valuable data – much less sensitive, personal health records – strong focus needs to be applied to how and where data is being stored, accessed, and used and by whom or what assets.
Organizations cannot retrospectively “threat hunt” for data that’s already been leaked. There is no product or tool that can find your already-leaked data, turn back the hands of time, and put everything back together again! That’s why data protection depends upon a proactive regime of data discovery, identification, classification, and protection to prevent breaches from occurring in the first place.
Classifications identify and track sensitive content by applying content fingerprints or tags/definitions to files and content. Some organizations may have existing data classifications set by solutions such as Titus, Boldon James, or Microsoft’s Azure Information Protection (AIP). Some DLP solutions offer the ability to both integrate with and leverage existing classifications in order to fast-track the overall process.
There are a few ways to integrate data classifications into your security practices, including (but not limited to):
- Content Fingerprinting: Build indexes of rolling hashes of your data to prevent sensitive or confidential information from leaving the organization by creating compliance policies around it.
- File/Data Attributes: Provides the ability to classify files based on keywords and dictionaries, file metadata, or content within the file/document itself.
- Optical Character Recognition (OCR): Extends DLP protection against tax paperwork, passports, credit card information, or personally identifiable data that could be uploaded or shared as images.
- Index Document Matching (IDM): Lets you fingerprint the content of sensitive corporate data in documents, such as Word, PDF, PowerPoint, or CAD documents, improving detection accuracy of sensitive data that would be difficult to find otherwise.
- Exact Data Matching (EDM): Performs the fingerprinting of structured sensitive data, designed to detect PII and other confidential data stored in a structured data file such as spreadsheet or CSV, with a very high detection accuracy and low false positive rates.
Particularly in the case of EDM, Skyhigh Security uses it to establish fingerprints – up to 6 billion cells – that protect sensitive user database records in a row and column format (typically extracted from a database in CSV format), build structured indexes of that data, and use DLP policies to prevent sensitive information from leaving the organization.
In this case, patient medical records (and more holistically, employee and/or customer records, etc) are typical examples of large and sensitive information groups that need protection. Although you can protect such records by matching patterns and dictionary terms, these methods of data matching require complex conditions and rule logic, which are prone to false matching.
Matching individual fields of a sensitive record, such as name, date of birth, unique patient identifier, and telephone number might not be useful, and can easily result in a false match. But matching two or more fields of the same sensitive record (for example, both name and social security number) within the same text (such as an email or a document) indicates that meaningful related information is present. EDM (Enhanced) fingerprints match the actual words in the defined columns within a certain proximity in a record (line or row) against the original user record, which prevents false matches.
Fundamentally, these should be bare minimum capabilities included within an enterprise-grade DLP solution and regime.
For existing customers, Skyhigh Security’s unified data protection delivers a visual representation of sensitive information that shows where it has been distributed, how it is being used, and where it has been exfiltrated across all cloud applications, web, private apps, email, and endpoints, highlighting data compliance risks. Skyhigh Security protects against data loss by applying classifications to data protection policies that trigger actions, generating incidents when sensitive data is identified.
Natively, Skyhigh Security’s Cloud Access Security Broker (CASB) platform supports built-in definitions, validations, and keyword information for healthcare data identifiers, including Australian Medicare Numbers, DEA Registration Numbers, National Drug Codes (NDC), National Provider Identifications (NPI), UK National Health Service (NHS) Numbers, and more.
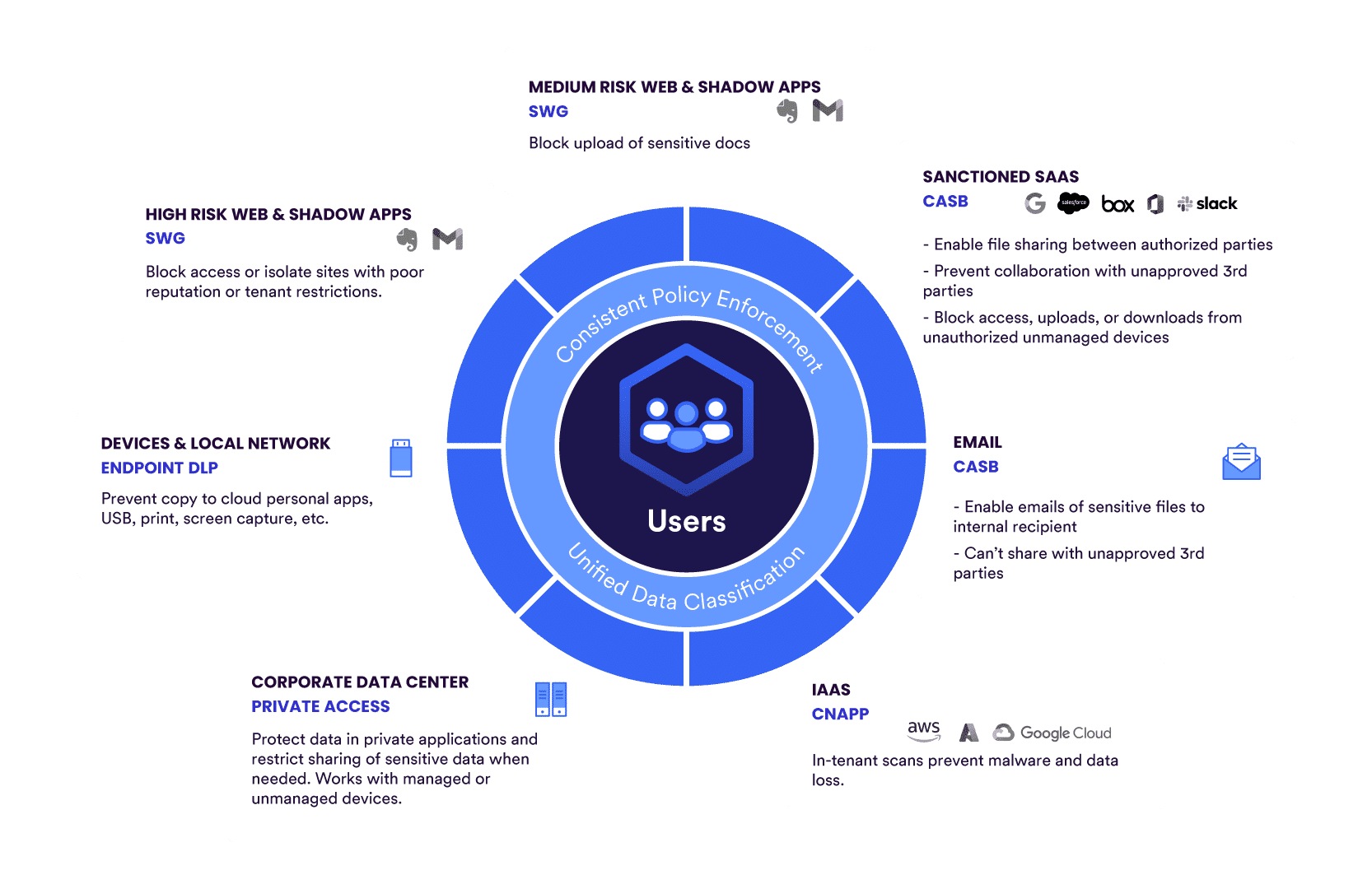
The reality is, continuously discovering, defining, classifying, and protecting your data isn’t a simple “set and forget” task, nor is it a superfast exercise if done thoroughly and correctly.
Data classification is one of the key factors of data protection and data privacy. Hence, by laying a strong foundation of common practices for data discovery, definition, and classification, organizations can apply more extensive and substantial data protections across potential leakage channels wherever they may be.
Use Skyhigh Security?
- Secure access to storage locations and private applications by implementing Zero Trust Network Access (ZTNA) capabilities.
- Define specific device profiles to continuously assess the security posture of connecting devices and requesting parties.
- Integrate, create, and apply DLP file classifications between Skyhigh Security and Trellix ePO.
- Apply built-in definitions, validations, and keyword information for healthcare data identifiers.
- Leverage existing Microsoft Azure Information Protection (AIP) classifications to protect sensitive, valuable data.
- Categorize files based on their confidentiality and enforce policies associated with that confidentiality level.
- Monitor your organization’s structured and unstructured data within databases, building fingerprints to help protect it at all times.
- Apply Exact Data Matching (EDM) fingerprints to protect sensitive user database records in row and column formats.
- Enable Optical Character Recognition (OCR) analysis to extract sensitive text and contents from supported image files.
- Scan and examine cloud services for any content that violates your DLP policies.
- Integrate with Boldon James, Titus, Box, and other support classification technologies.
- Define match criteria for policy violations, including file metadata, regular expressions, and more.
With over 11 years’ worth of extensive cybersecurity industry experience, Rodman Ramezanian is an Enterprise Cloud Security Advisor, responsible for Technical Advisory, Enablement, Solution Design and Architecture at Skyhigh Security. In this role, Rodman primarily focuses on Australian Federal Government, Defense, and Enterprise organizations.
Rodman specializes in the areas of Adversarial Threat Intelligence, Cyber Crime, Data Protection, and Cloud Security. He is an Australian Signals Directorate (ASD)-endorsed IRAP Assessor – currently holding CISSP, CCSP, CISA, CDPSE, Microsoft Azure, and MITRE ATT&CK CTI certifications.
Candidly, Rodman has a strong passion for articulating complex matters in simple terms, helping the average person and new security professionals understand the what, why, and how of cybersecurity.
Attack Highlights
- HCA Healthcare reported that an unauthorized actor stole data across ~11 million patients in 20 states, including Florida, and posted it on an online forum. The list posted on the forum contained 27 million rows of data.
- According to HCA, the data comprises patient names, address information (including city, state, and ZIP code), patient email addresses, phone numbers, dates of birth, gender, and patient service dates, including details about locations and information related to upcoming appointments.
- HCA believes the data was stolen from an external storage location used to automate email messages.
- HCA has not disclosed the exact date it became aware of the data theft.
