Skyhigh Remote Browser Isolation
Malware protection. Safer browsing.
Seamless user experience.
Prevent web-based threats from reaching endpoints
What makes us better than the rest
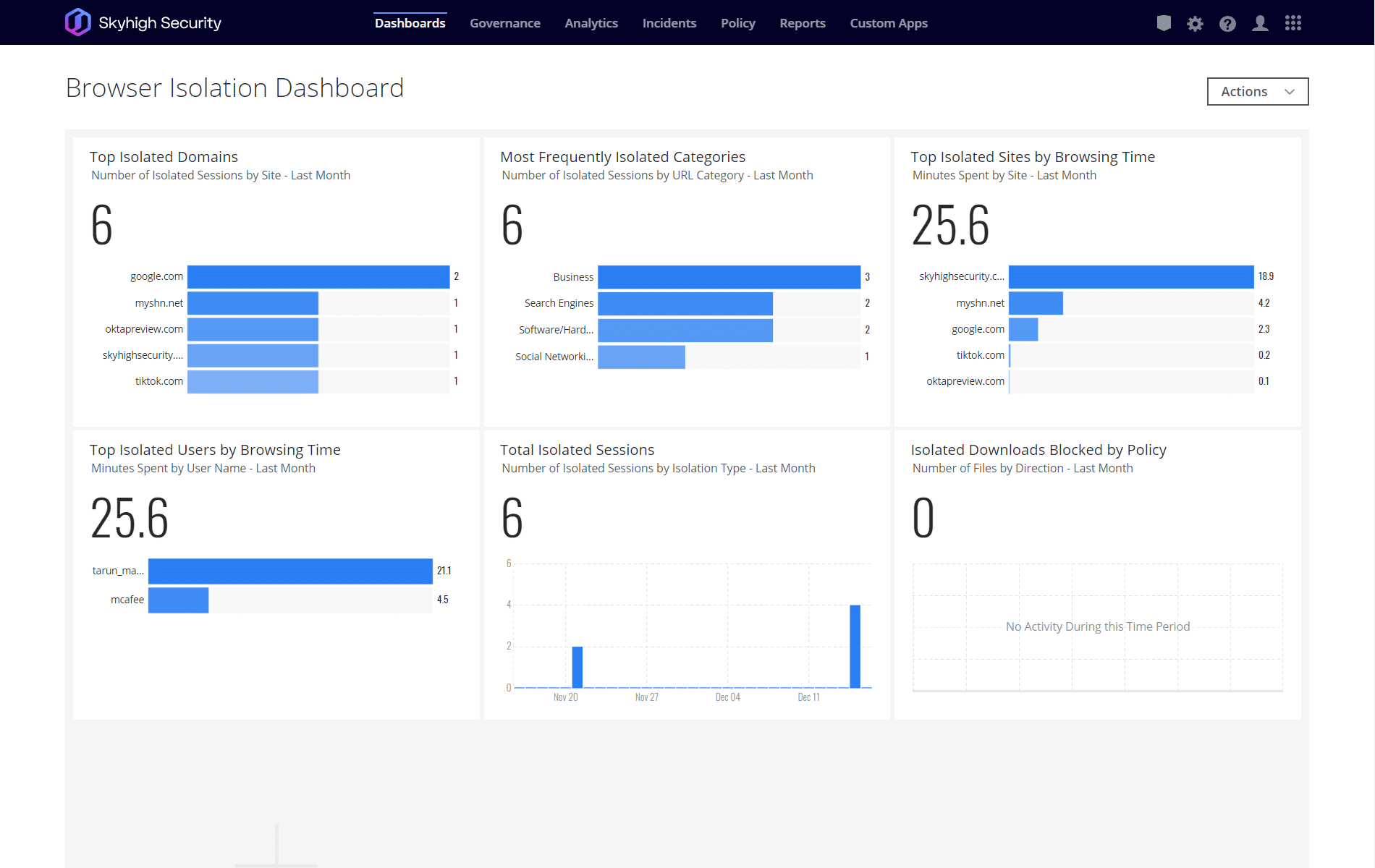
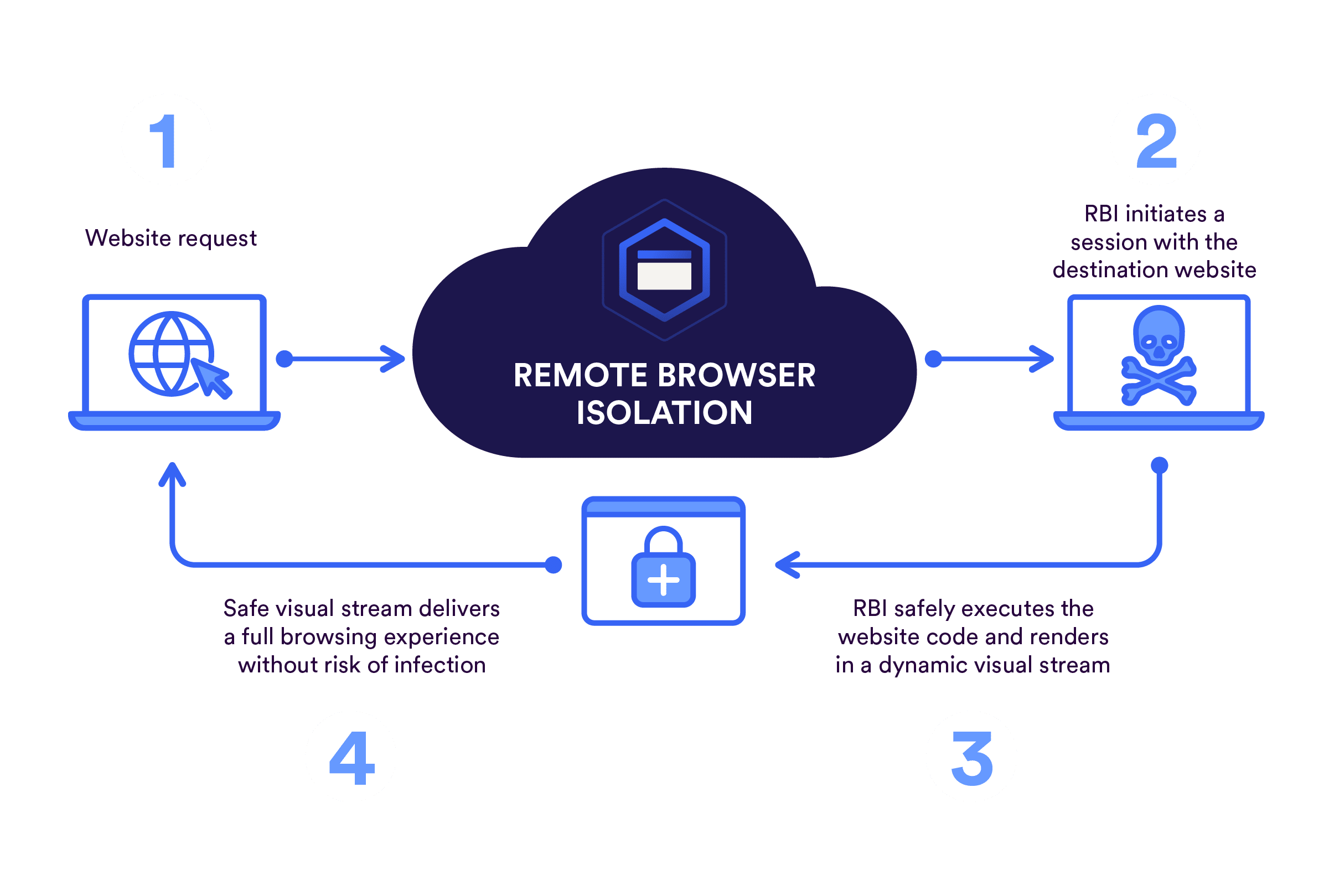
Skyhigh RBI automatically mitigates risk from unknown websites, ensuring threats do not reach endpoints
Read the WhitepaperMinimize Your Cloud Attack Surface
Skyhigh Security prevents unknown threats from ever reaching endpoints by integrating intelligent yet transparent Remote Bowser Isolation, leveraging powerful machine learning analysis on real-time telemetry from over one billion sensors.
Integrated RBI Capabilities
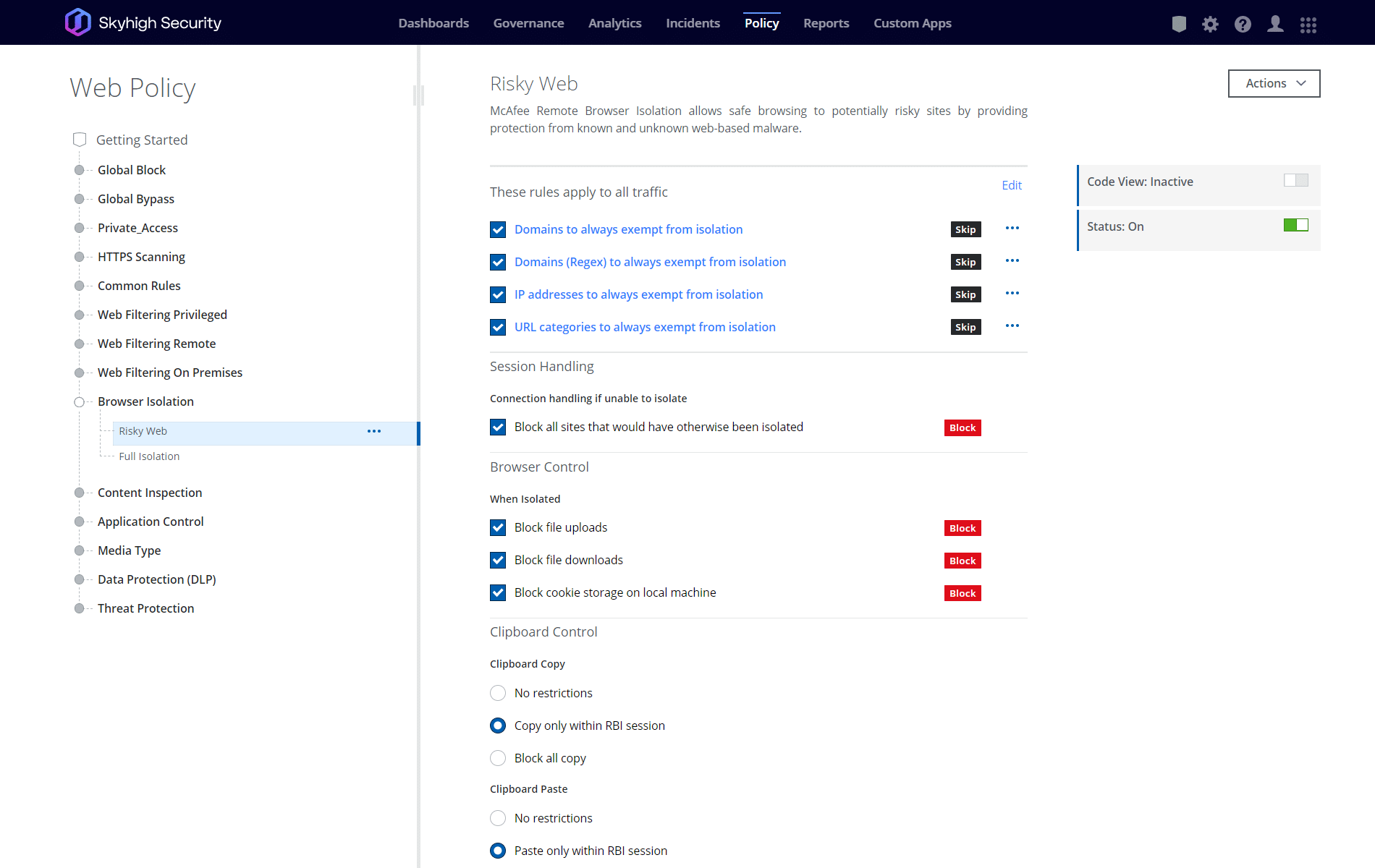
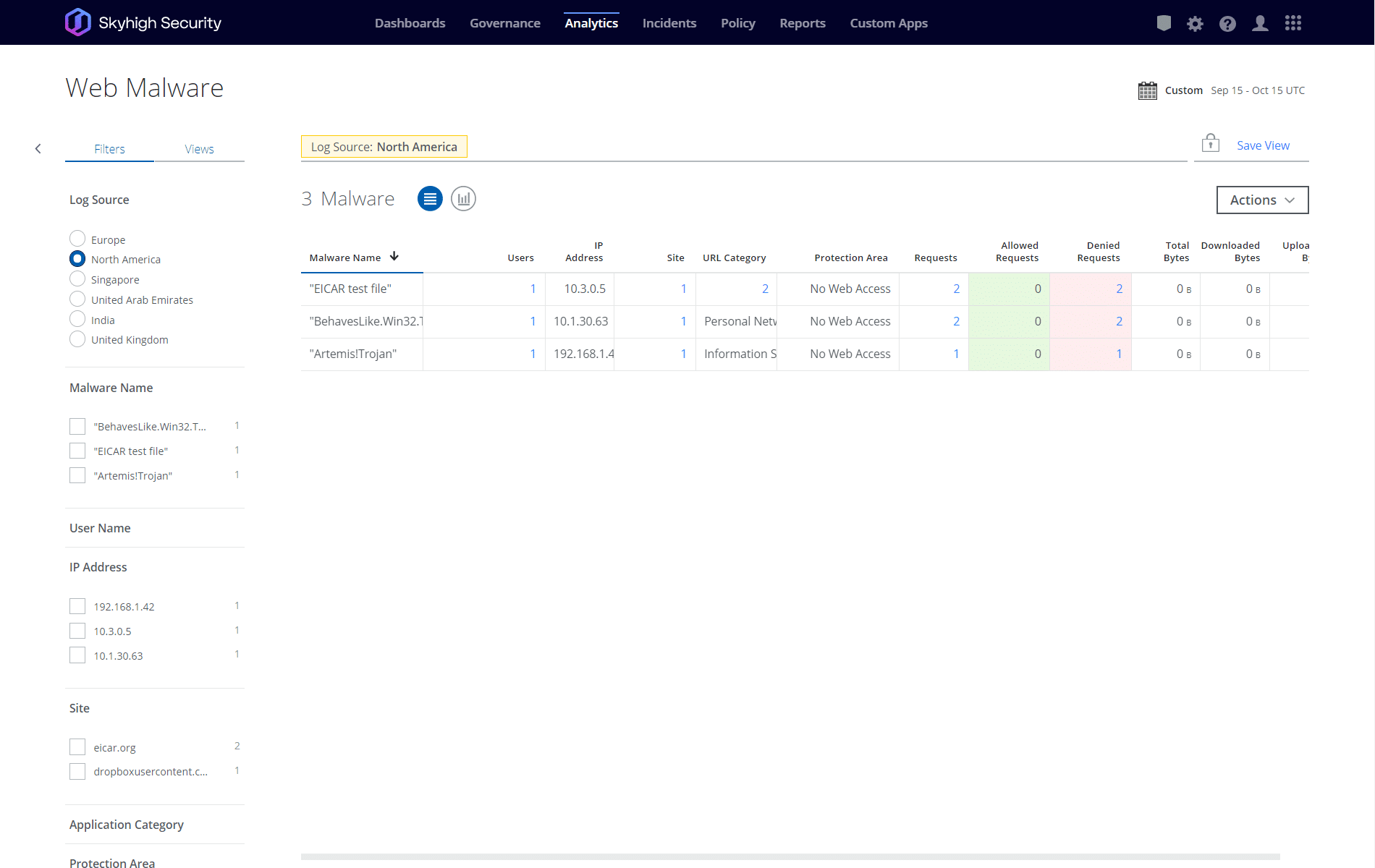
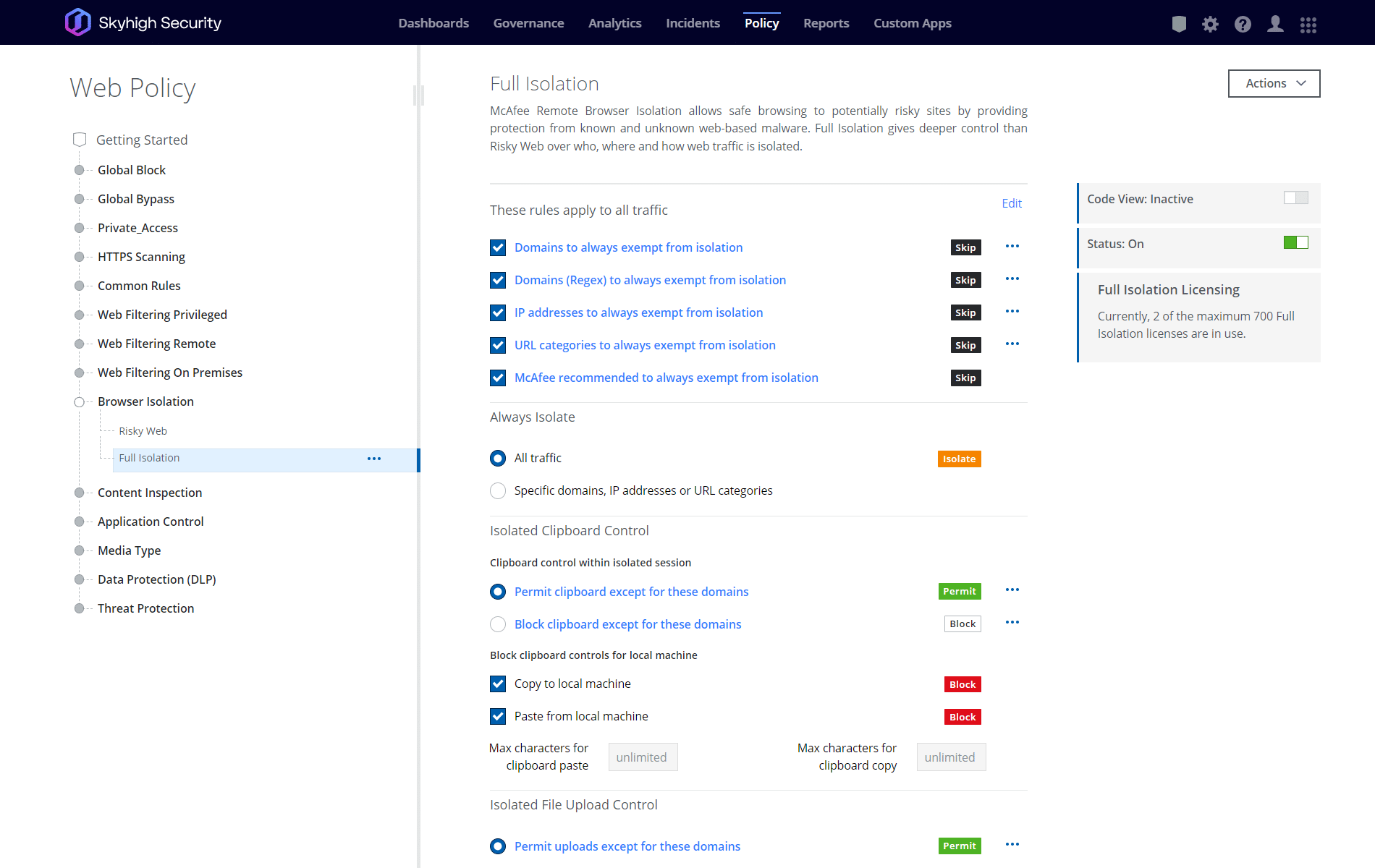
What RBI technology can do for you
Because no local code execution happens on the user’s computer, users are protected from all malicious websites, links, emails and adverts.
Administrators can finely control which files users are permitted to download. All permitted downloads are first scanned to eliminate threats.
Organizations can obtain analytics into users’ web activities, which can be used for compliance monitoring and to detect insider threats and unproductive employees.
Isolating all web content results in fewer security alerts and false positives that need to be investigated.
The effects of a malware infection can be severe and require a substantial amount of money and time to fix. Isolated browsing protects your network completely from web-based malware.
Awards and Recognition
Resources